Sensitive data can flow into apps you don’t control. Find unmanaged SaaS and secure it before exposure.
Of breaches involve data sitting in shadow IT
Average number of shadow apps for large enterprises
Shadow SaaS accesses sensitive data
Shadow SaaS security starts with discovery. Uncover every app in use, control access and data flows, and reduce risk across the organization.
WATCH A DEMOCorrelate browser, email, and IdP signals for complete app visibility.
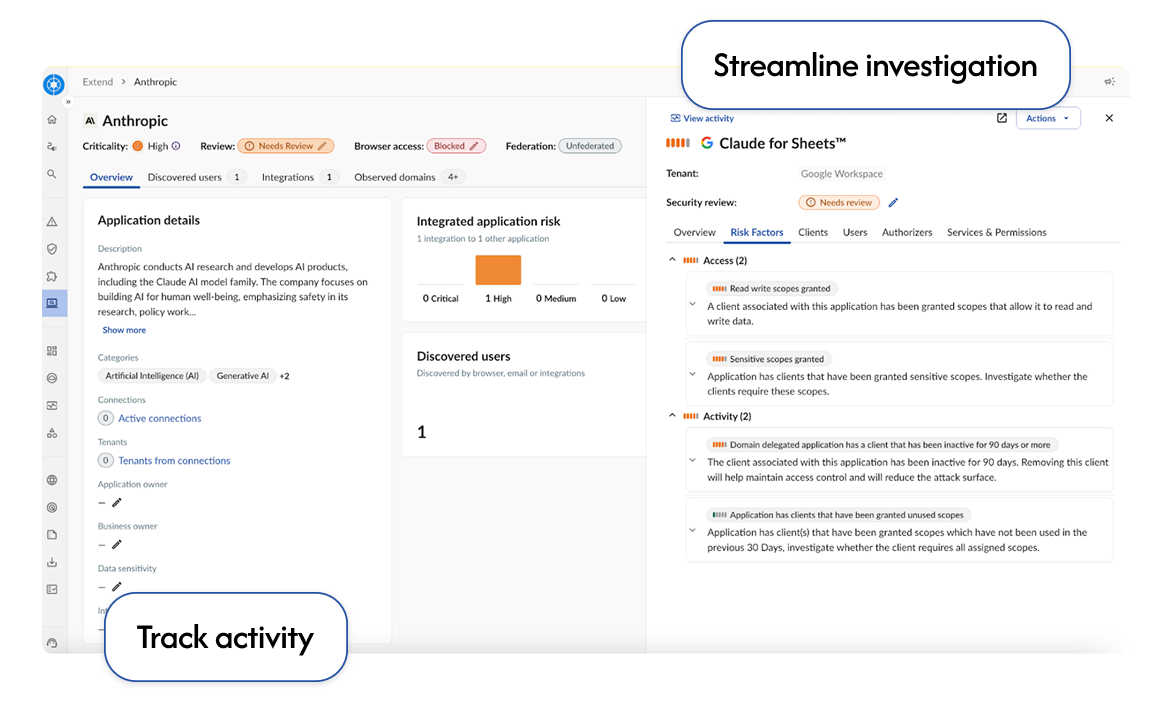
Get context on users, activity, and risk factors to prioritize what matters.
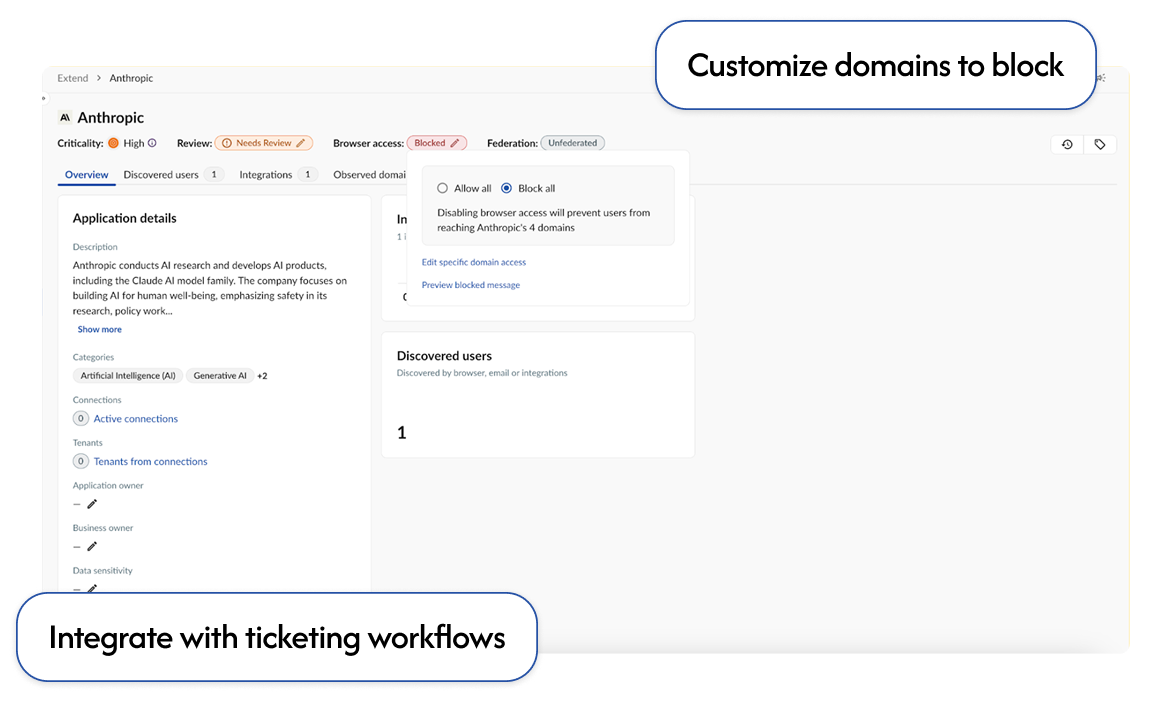
Federate apps to your IdP or block browser access with one click.
Track new apps and usage changes automatically, without friction.
Create a comprehensive and live inventory of all SaaS applications in your environment.
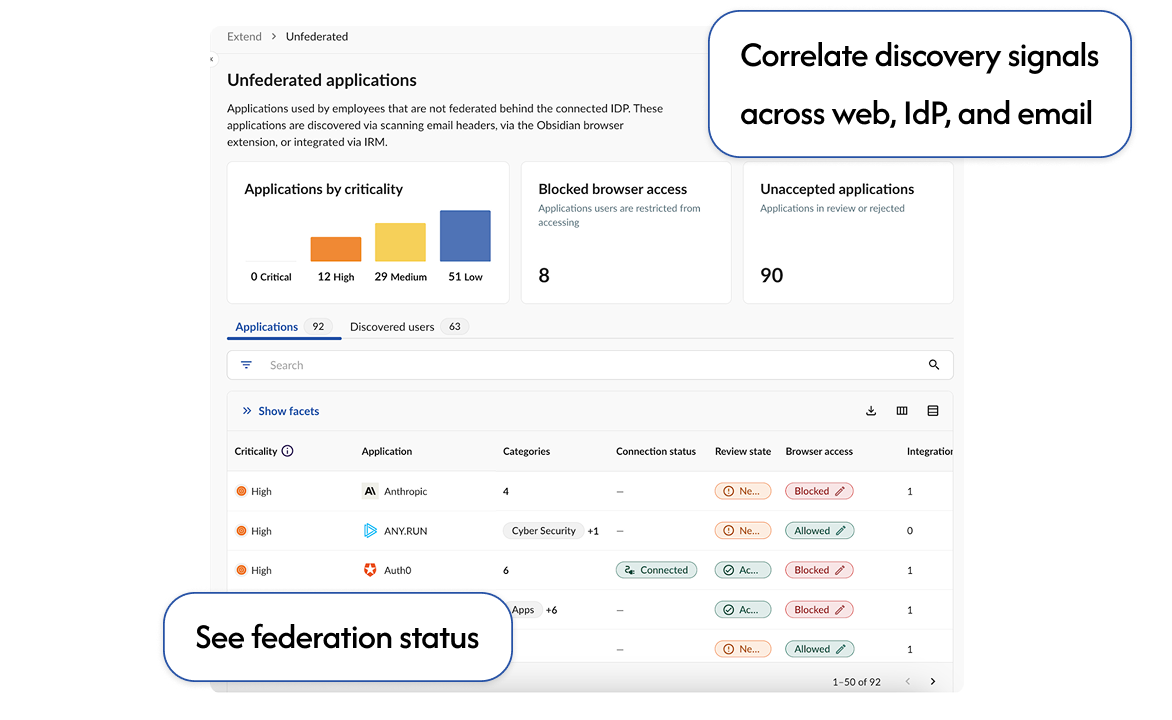
Get key context into each unfederated app, including app type, users, activity, integrations, and risk factors.
Leverage flexible controls to warn or block users from accessing risky apps.