

Users can unintentionally expose SaaS data by granting overly broad permissions or creating public links. Identify and remediate risky misconfigurations to prevent unauthorized access across every app.
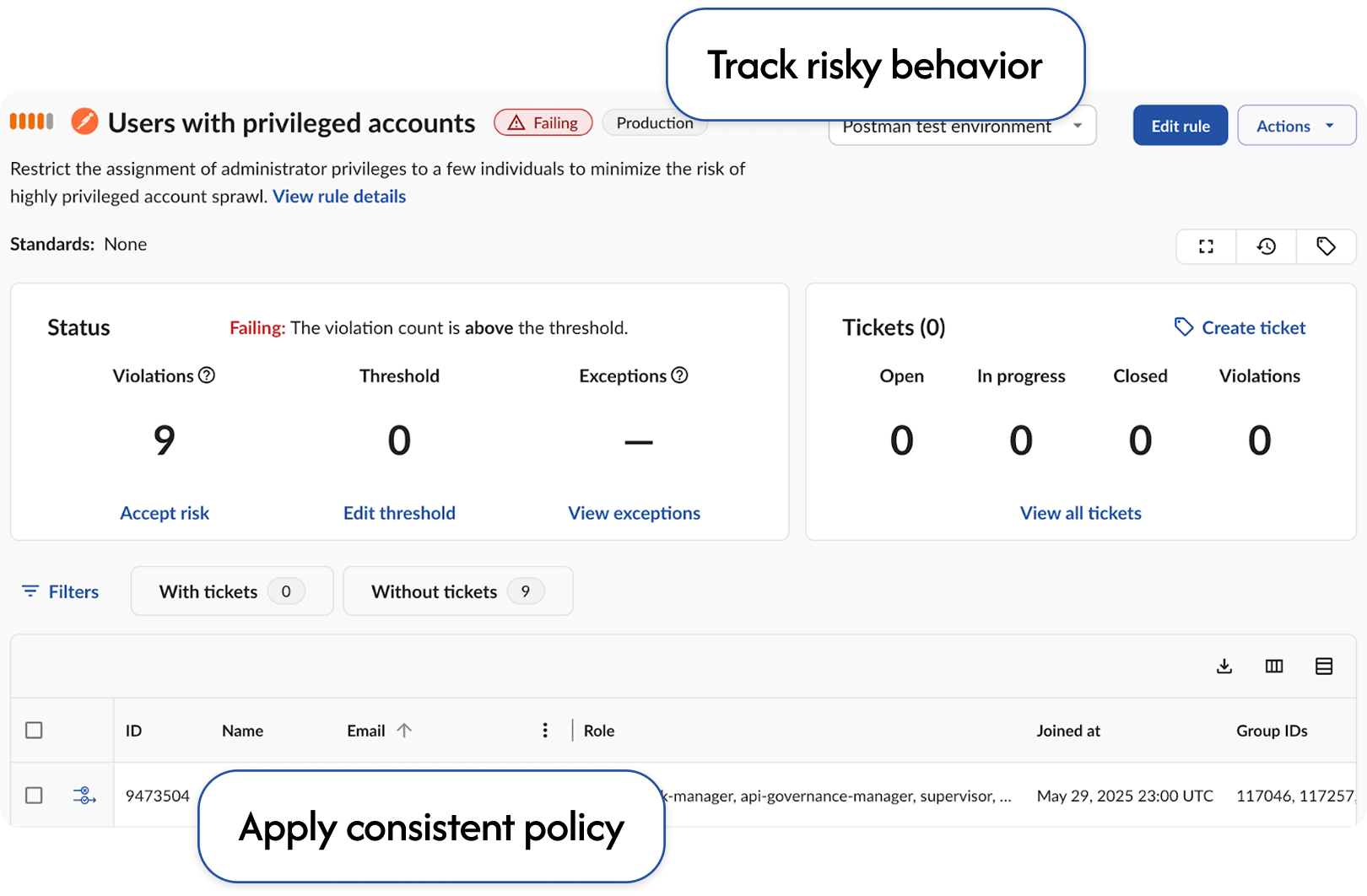
SaaS accounts are over-privileged
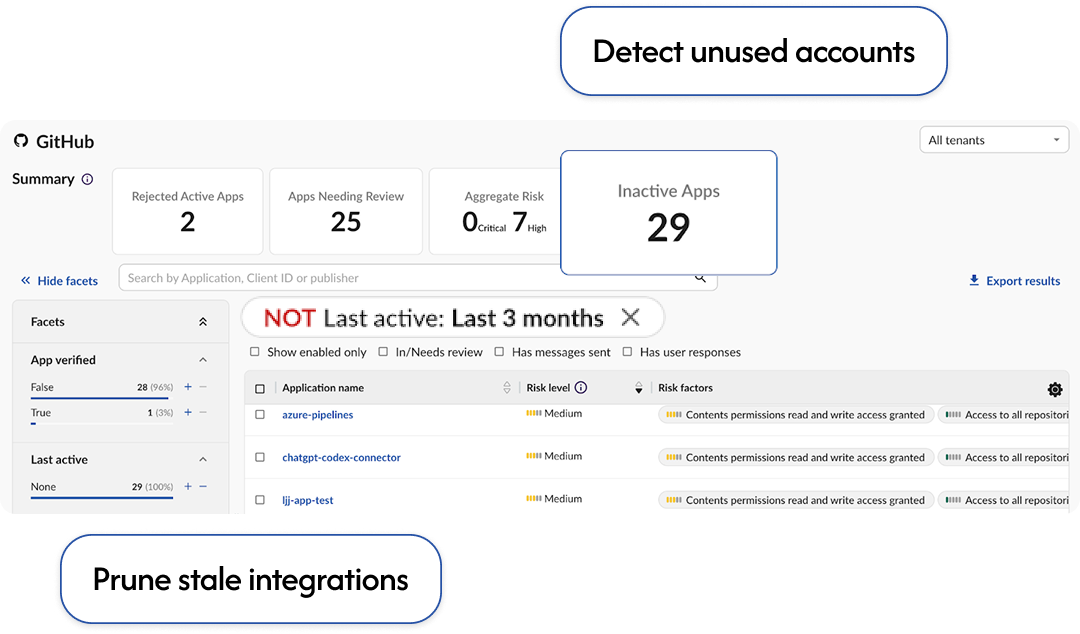
SaaS integrations unused for +90 days
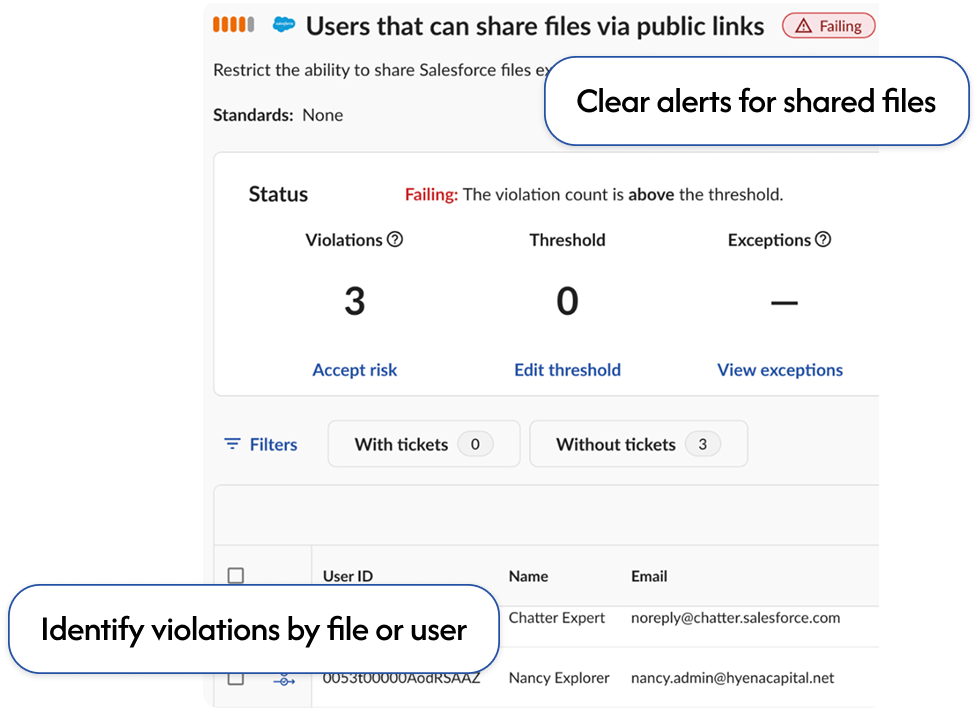
Public files uncovered at one organization
See what access is used, what is leftover, and why exceptions exist so you can cut excess privilege, right-size access, and shut down every instance of unauthorized data exposure.
watch A DEMOHarden privileges and permissions to curb unsanctioned access in SaaS.
Find and fix public links and anonymous access pathways before your data is exposed.
Detect and deactivate idle accounts and stale integrations.
Cut the blast radius and minimize breach impacts with least privilege for SaaS.
Find evidence of lingering privileges and allow only necessary permissions in SaaS.
Reduction in over-privileged accounts
Identify and remove unnecessary access permissions.
decrease in SaaS attack surface
Constantly track open links and risky data sharing settings to curb unsanctioned access.
reduction in publicly available files
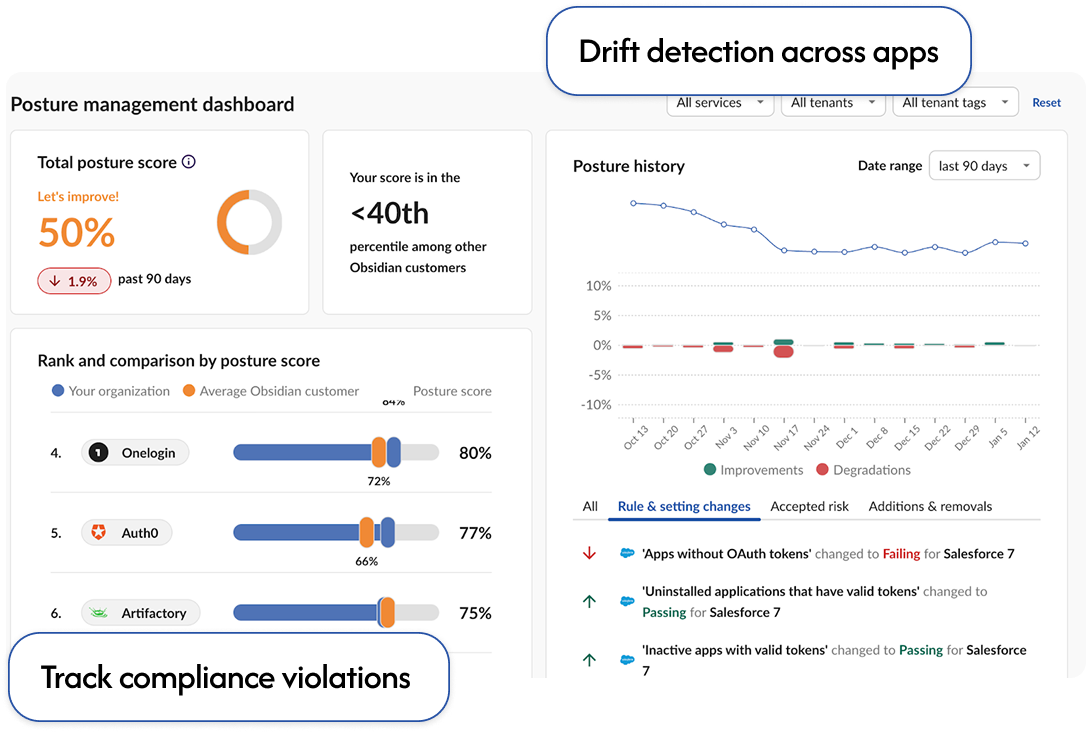
Continuous monitoring of SaaS settings and privileges plus audit-ready reports for standards like HIPAA and DORA.
reduction in audit prep time