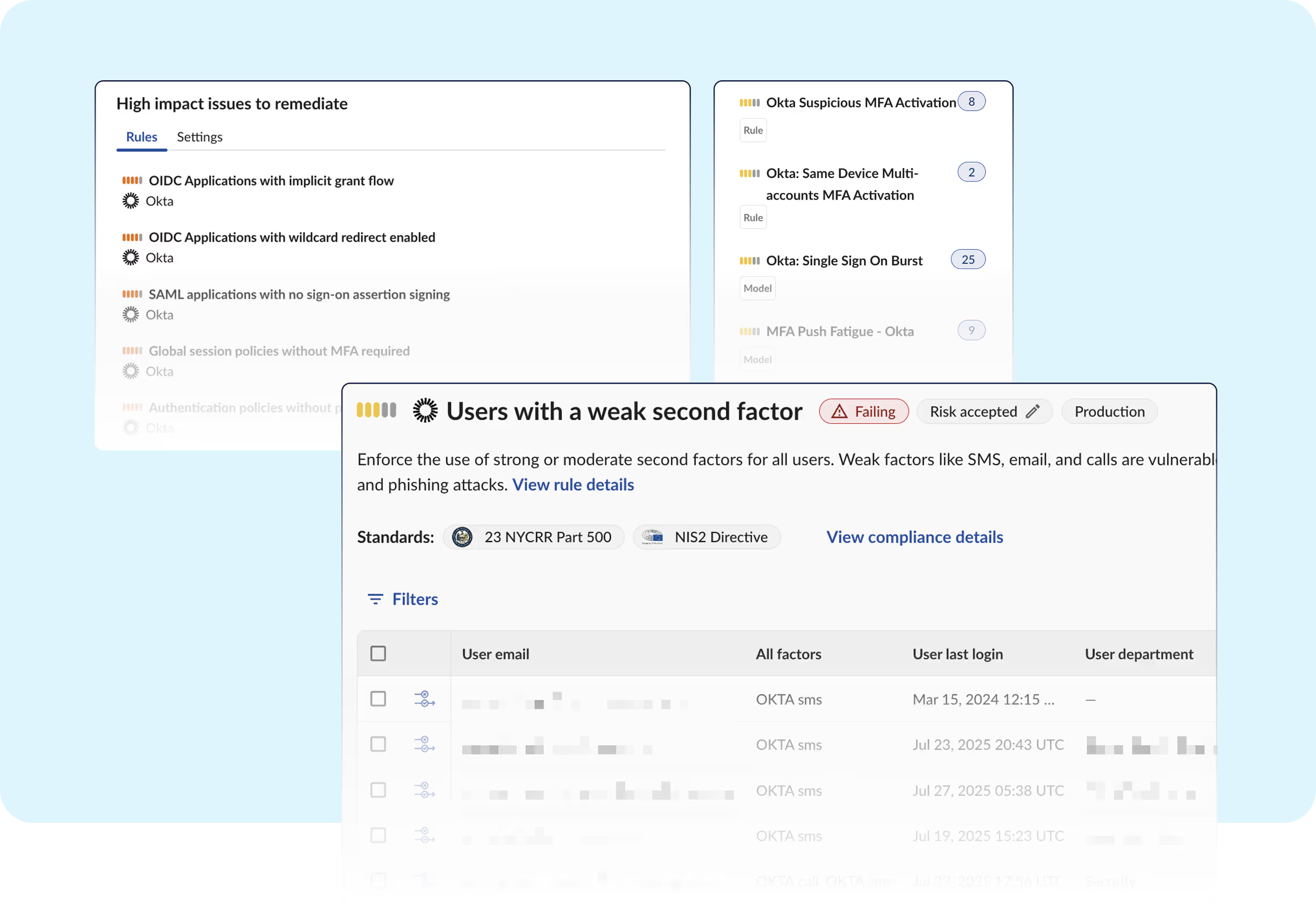
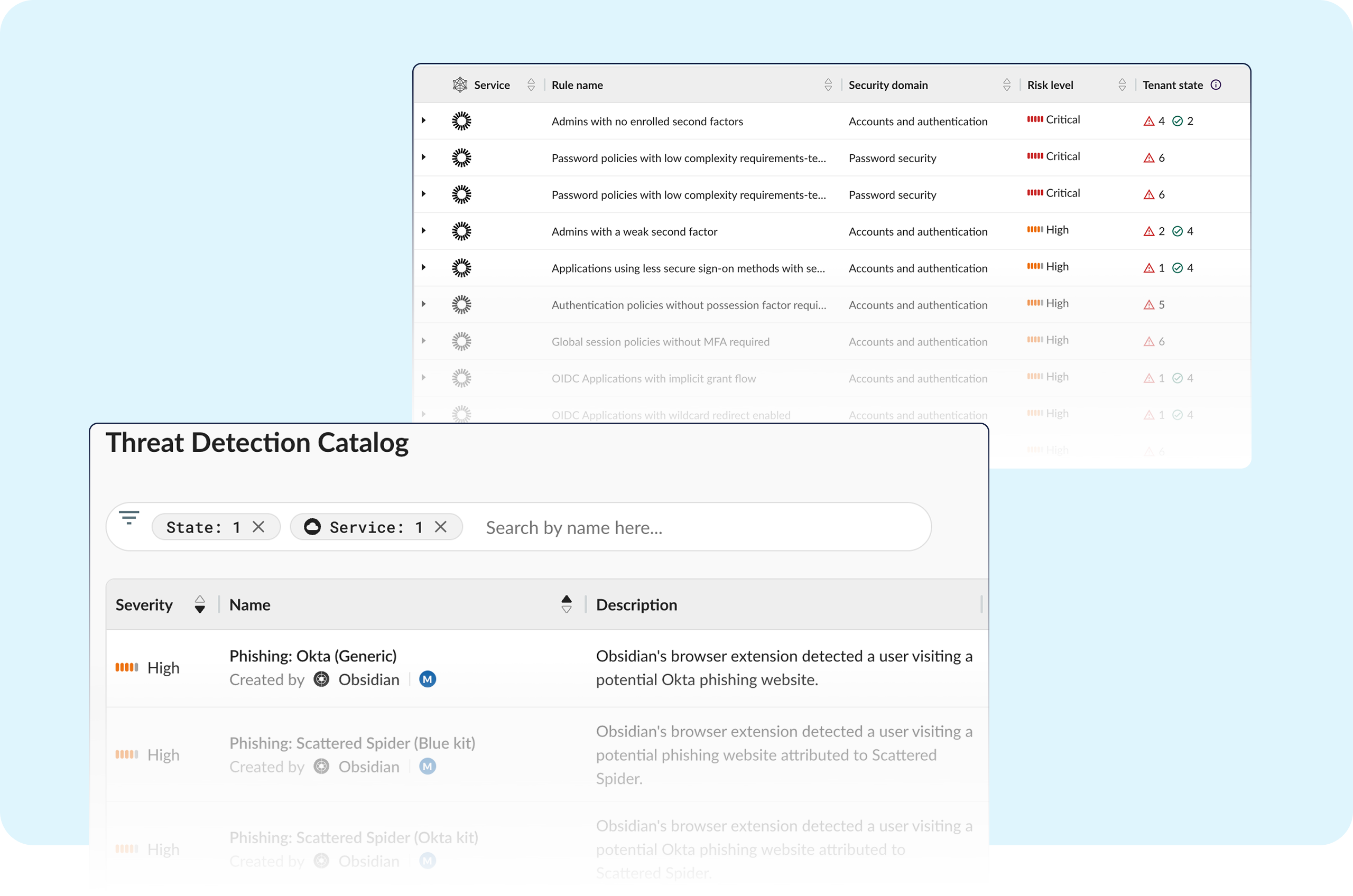
With complex identity flows, long access tokens, and cross-app connections, securing Okta by hand is error-prone and slow.
- Manual auditing of MFA use, authentication policies, and app assignments is tedious
- Adversary-in-the-middle (AiTM) phishing attacks bypass MFA like Okta Fastpass without security oversight
- No easy way to detect or respond to social engineering attacks where attackers enroll their own device for MFA with weak authentication