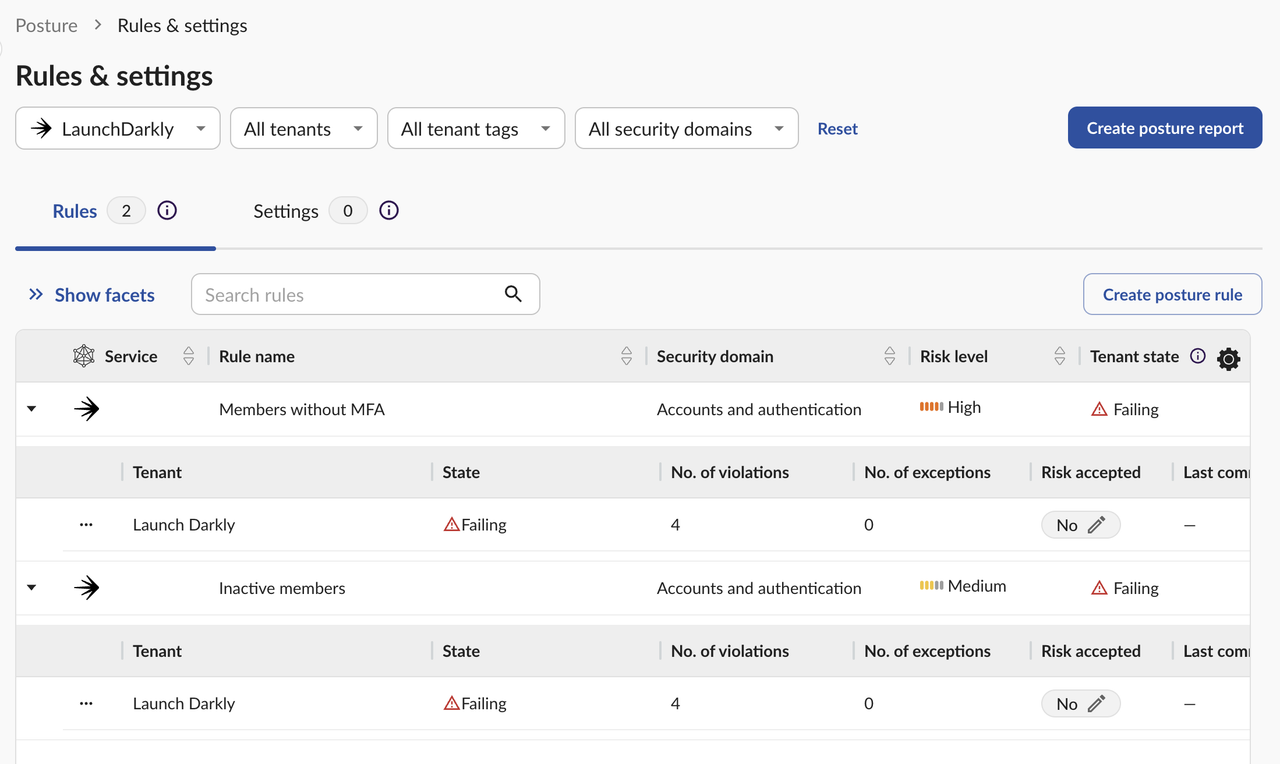
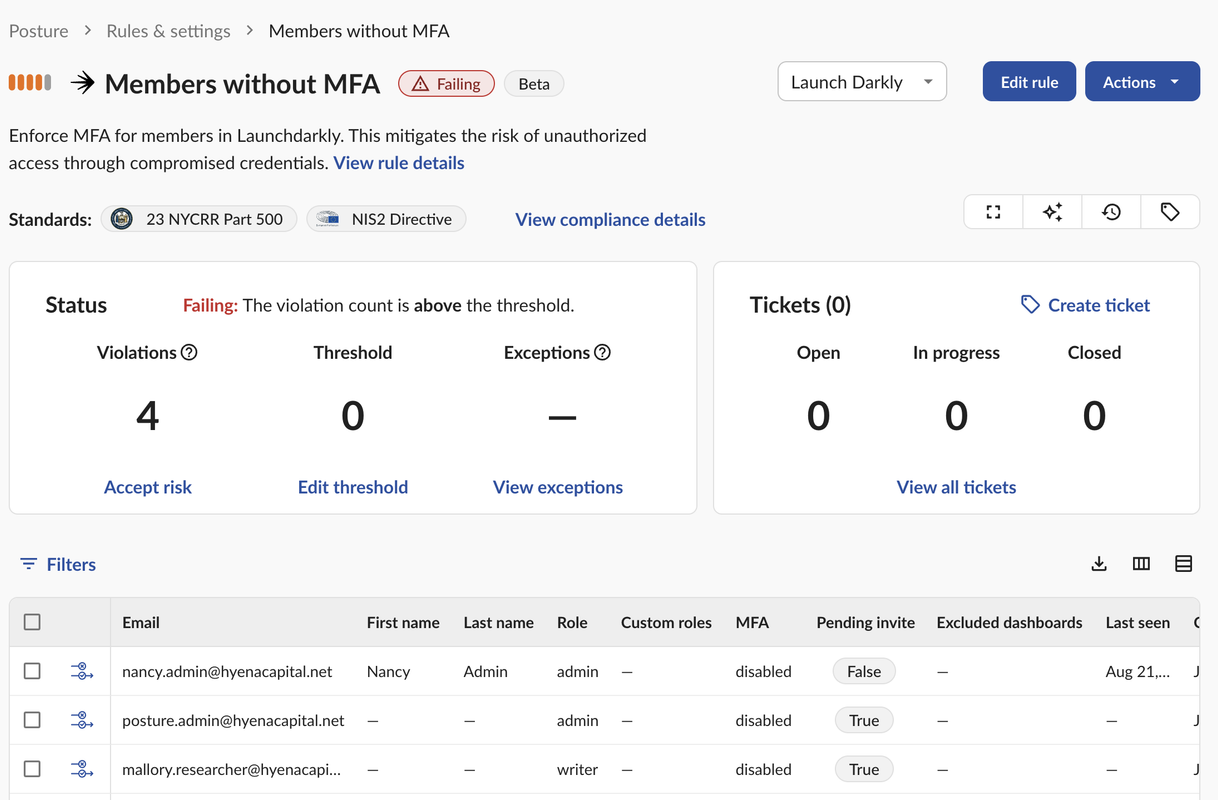
Trying to protect SaaS without the right tools or context adds complexity and ignores risk:
- Manual review does not scale: Security settings and permissions are unique for every vendor, demanding significant time and expertise to manage across SaaS
- SaaS requires continuous monitoring: Access and privileges persist and evolve beyond intended use without monitoring or lifecycle enforcement, growing the attack surface
- Disparate security leaves gaps: No centralized visibility or control over third-party app authorizations, OAuth scopes, or integration activity can leave risks unnoticed
- Attackers are focused on SaaS: Compromise of high-privilege tokens or integrations can grant attackers persistent, organization-wide access to sensitive data