SaaS breaches have increased 4x in the last year. We have seen a sequence of breaches that have impacted major SaaS vendors, such as Microsoft and Okta. Snowflake has been in the news recently due to attacks targeted at customer-owned systems. The common thread of these incidents is identity. The attackers are not breaking in, they are logging in.
SaaS is now a very active space, where attacks are occurring across the spectrum, from targeted APTs to financially motivated attackers, and every company needs to carefully review their SaaS security program. As with any SaaS application, customers have a shared responsibility with the provider to make sure the data is safe.
Snowflake is a critical component of many businesses with the platform at the core of data collaboration, AI, personalization and customer engagement initiatives. Securing this critical business infrastructure against threats is critical, but can also be complex without the requisite expertise.
If you are looking to immediately address any unauthorized access to your Snowflake environment, review our accompanying blog that discusses immediate steps you can take to minimize impact.
Steps to Securing Your Snowflake Environments:
Here are steps customers can take to ensure their Snowflake instances are safe.
A) Harden identities with access to your Snowflake environment
Configuration drifts and over-privileged users often introduce weak spots that lead to breaches. In fact 1-in-5 SaaS breaches we see stems from basic posture issues. The recent Microsoft breach leveraged a test account to drive the compromise.
Ensuring the right posture for your Snowflake environment includes several steps. However, here are 3 critical steps:
- Eliminate users bypassing the IdP. There are few reasons for local access. Review and eliminate local access accounts, except any necessary ones. Attackers use local access as backup pathways. Hence, it’s crucial to monitor these.
- Make multi-factor authentication (MFA) mandatory. Why wouldn’t you in this day and age? Ensure all users, especially privileged accounts, have MFA enabled. For any service accounts, use client ID and secret – not password – for the handful of legitimate local accounts (e.g. breakglass accounts) implement Snowflake’s native MFA.
- It might also help to restrict where users can access your environments from. For example, any local account access could be restricted to users from specific IP address or IP ranges. Define network policies to restrict access to specific IP or range of IPs.
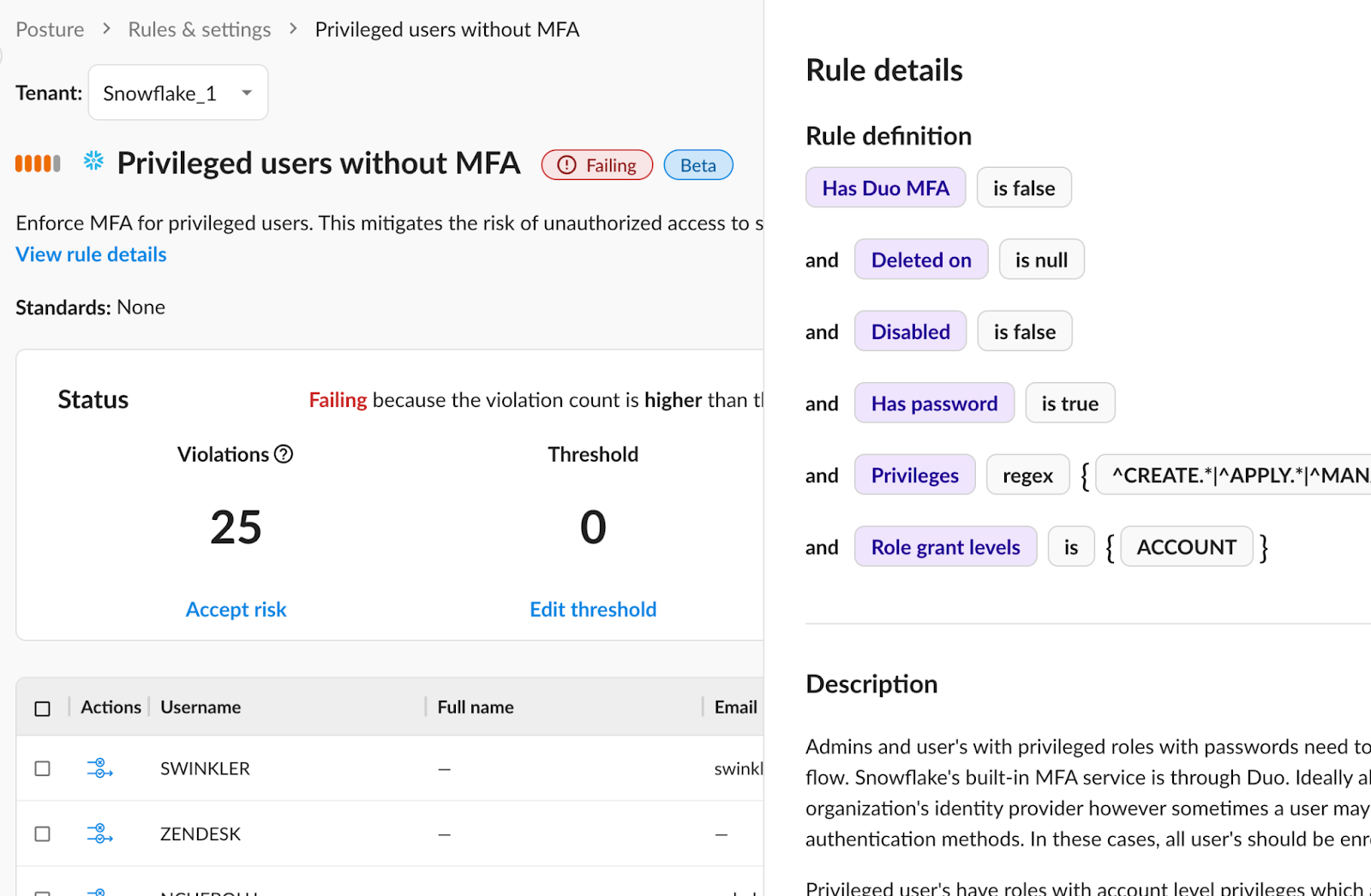
B) Eliminate unused identities
Inactive identities are ripe ground for attackers. Identify and eliminate inactive accounts – prioritize privileged accounts first.
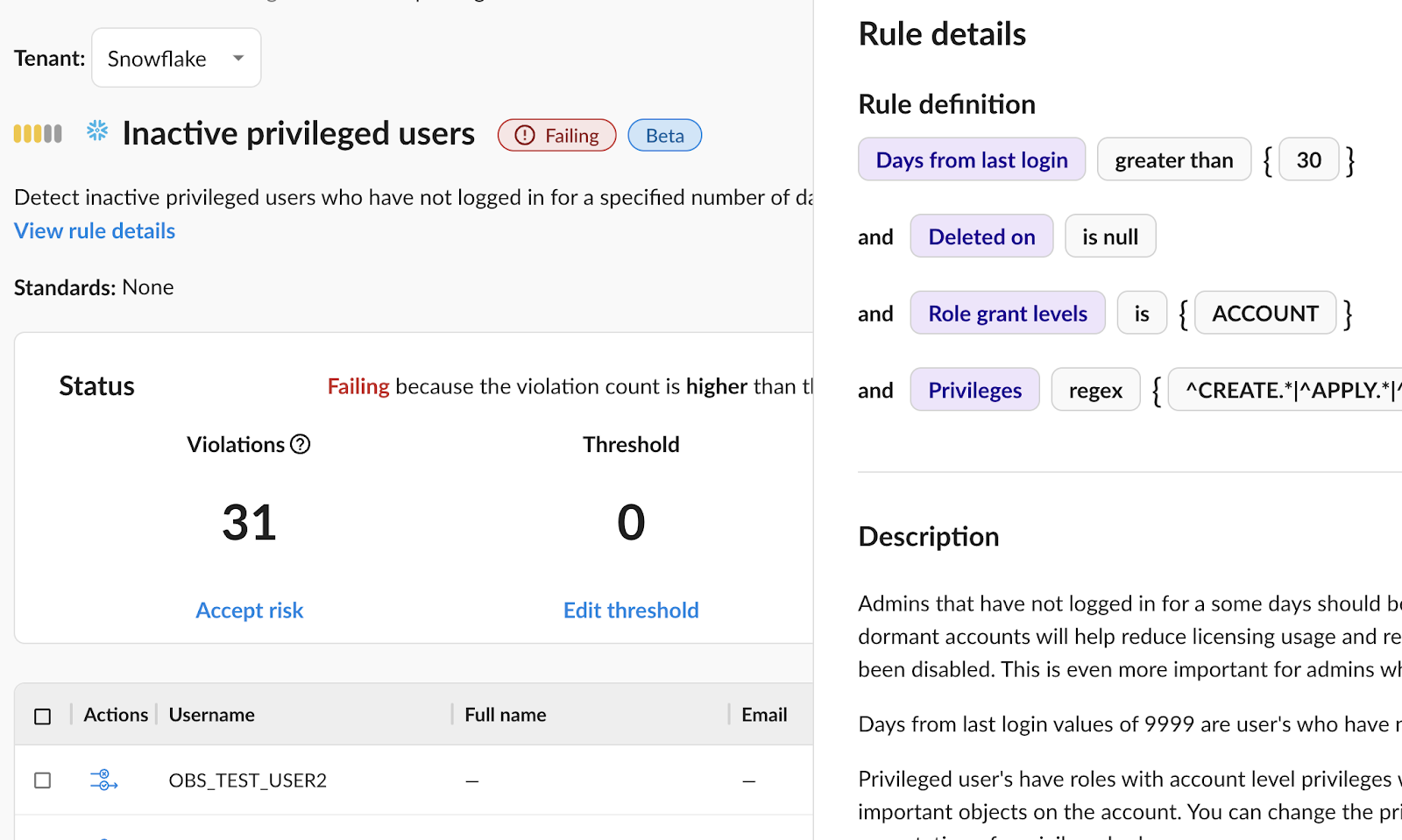
C) Govern data movement within the Snowflake environments
Data is at the heart of Snowflake. Managing data movement is important to allow value creation, but governing is equally important to disallow data exfiltration (MITRE ATT&CK TA0010). An employee may unknowingly (or knowingly, if an attack is using stolen credentials) export data to a location that is unapproved by the organization’s security teams.
Organizations can and should restrict data export from their accounts to external cloud storage, internal locations, and also govern the locations for data export through Snowflake account level parameters such as:
- PREVENT_UNLOAD_TO_INLINE_URL
- REQUIRE_STORAGE_INTEGRATION_FOR_STAGE_CREATION
- REQUIRE_STORAGE_INTEGRATION_FOR_STAGE_OPERATION
- PREVENT_UNLOAD_TO_INTERNAL_STAGES
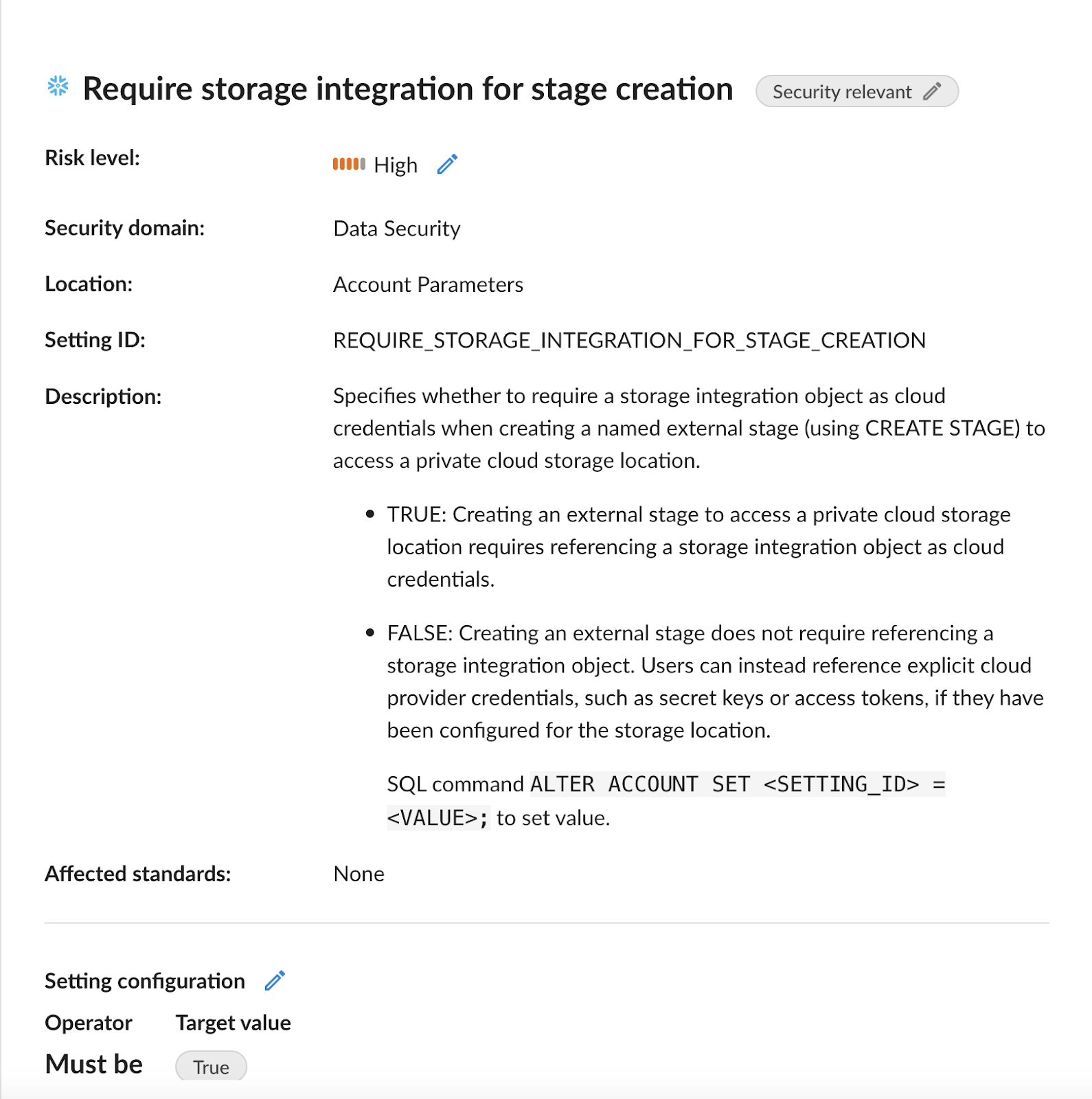
Additionally, organizations must also identify and manage connected applications that may be using less secure authentication methods to access data from Snowflake environments.
D) Monitor and protect users with access to Snowflake
Hardening and prevention are the first step in ensuring security of your Snowflake environments. They minimize the risk of breaches. However, it’s equally important for organizations to monitor users that have access. These include preventing spearphishing threats targeting Snowflake administrators and users and monitoring these user accounts for abnormal activities.
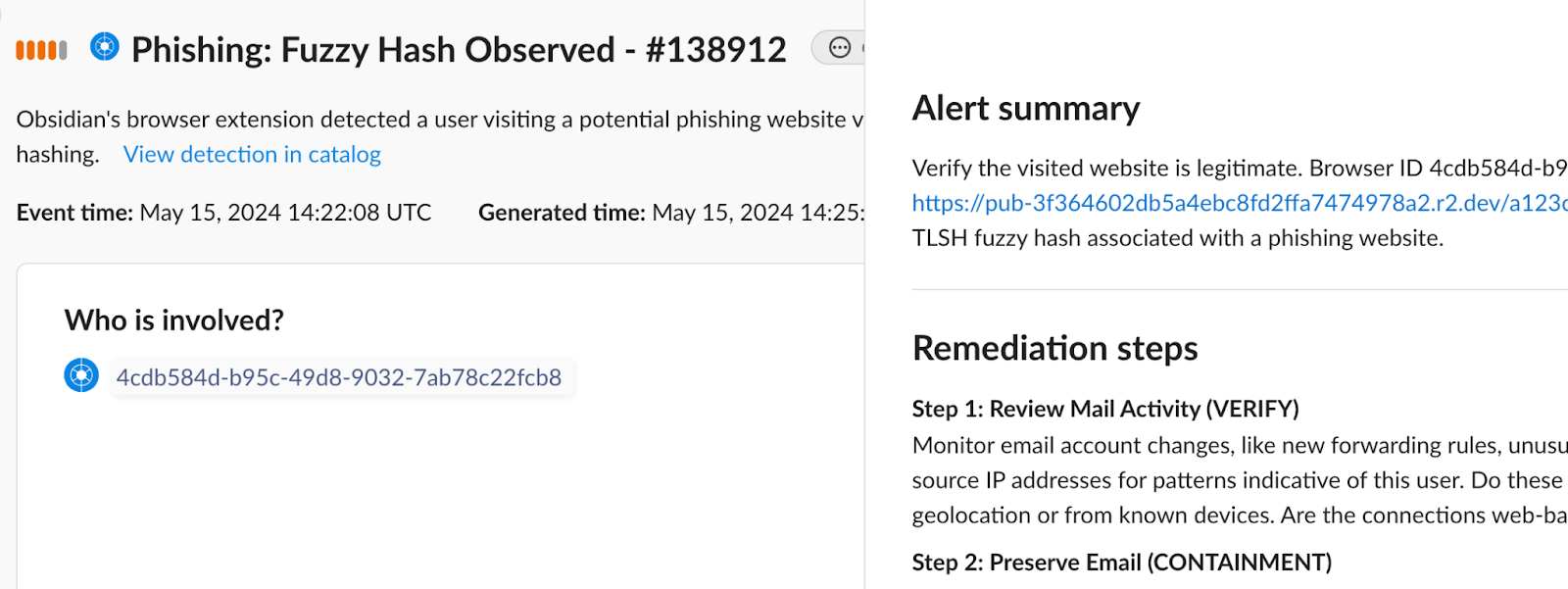
Or if you have indicators from your threat intelligence provider, you could also hunt for suspicious activities within your account.
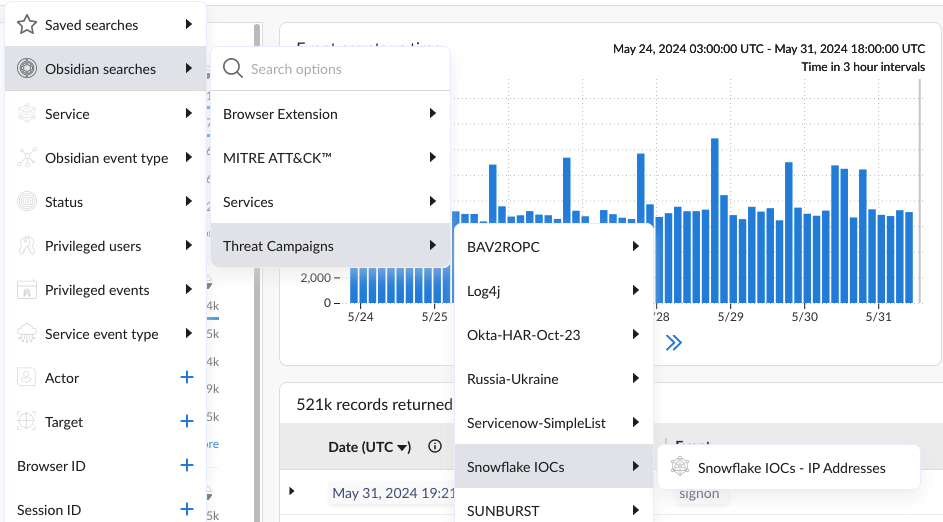
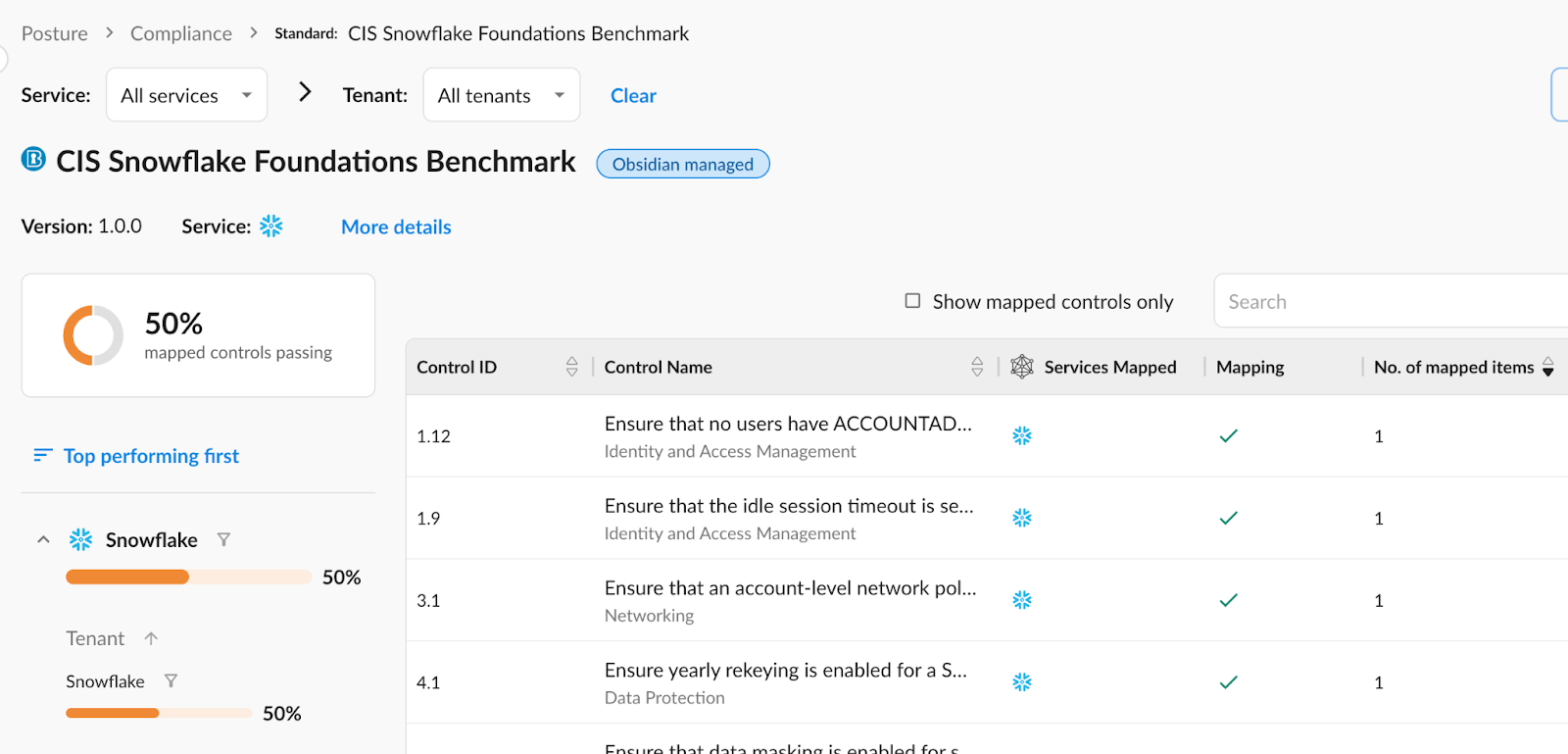
E) Align with Snowflake CIS benchmarks
A simple step that you can take in addition to the above is to align with the Snowflake CIS Benchmarks to prevent unauthorized access, enforce least privilege access, and mitigate data exfiltration risk.
Next Steps
SaaS applications aren’t static. Applications evolve, configurations change, identities get introduced, and attackers change their patterns. Your program needs to be continuous to keep up with your SaaS. In other words, you need automation to scale this across all your SaaS applications.
Obsidian has helped several organizations automate their workflows and ensure security of their Snowflake environments. To learn more about how Obsidian can help you or to get an assessment of your Snowflake deployment contact us today.




