Just as bank robbers target banks, nation-state actors now focus on identities within SaaS platforms because that’s where the valuable data is. It’s also easier than compromising traditional endpoints.
In February 2024, the Five Eyes (FVEY) intelligence alliance (Australia, Canada, New Zealand, the United Kingdom, and the United States) issued a warning about a cyber espionage group associated with the Russian intelligence service. This group has shifted from using traditional endpoint-focused malware to targeting identities within SaaS platforms as their primary method to gain initial access.
The full advisory can be found here.
A closer look
Nation-state actors have realized what we at Obsidian Security and, unfortunately, eCrime adversaries (such as Scattered Spider) have known for quite some time now:
- Organizations, both private and public, and governmental agencies are entrusting their data to SaaS and public cloud services. Not planning or transitioning, but already there.
- Targeted attacks on end users are an easy way to gain initial access, bypassing MFA, using well-established techniques such as Adversary in the Middle (AiTM) attacks, SIM Swapping and MFA Push Fatigue.
- Owning a user’s credentials/session allows an adversary to easily move laterally by way of the “federated” trust relationship that other applications have established with an organization’s Identity Provider (IdP). This includes the ability to jump from SaaS to on-premises through VPN services; something Obsidian has seen actively being used by adversaries today.

As a result, these nation-state actors are finding it easier to gain initial access to these platforms, for two key reasons:
The “shared security model” is not widely understood
Many organizations use 3rd-party SaaS platforms to transfer risk to the vendor. They assume the vendor secures their information, acting as custodian within the application. However, this assumption is incorrect. The “shared security model” mandates that subscribers set up their tenancy securely. Subscribers are responsible for ensuring secure access to their information. This misunderstanding often leads organizations to underestimate required security resources for monitoring and securing their SaaS tenancy.
SaaS security is unique
Its browser-based access and async session management require storing session tokens in the user’s browser and sending them with each request. This exposes active session tokens to theft by malware and AiTM attacks.
At Obsidian, we focus intensely on these SaaS attacks. We detect and respond to them before they gain popularity among eCrime actors and now nation-state operators. Obsidian handles dozens of active global Incident Response cases weekly involving these tactics.
Alarmingly, strategies like AiTM and MFA Push Fatigue succeed in over 51% of SaaS breaches. The remaining 49% involve SIM Swapping, Integration Abuse, and Endpoint Compromise.
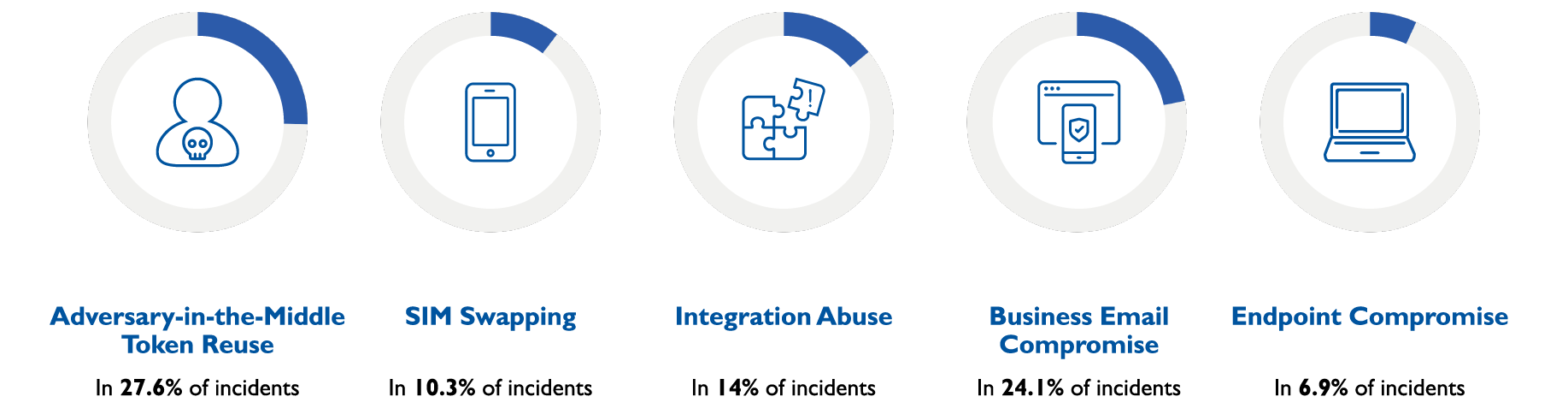
Obsidian’s approach
Obsidian provides comprehensive threat detection and prevention capabilities. Traditional SSPM vendors focus mainly on Posture Management, covering just 15% of breaches. Obsidian addresses the remaining 85% from residual risk in SaaS security incidents.
As highlighted by the recent Five Eyes advisory, Obsidian’s SaaS threat modeling swiftly identifies session theft and triggers response workflows or playbooks, or can proactively suspend compromised accounts. Conventional tools like Endpoint Detection and Response (EDR), Cloud Access Security Broker (CASB), or Secure Access Service Edge (SASE) lack the capability to offer such comprehensive protection.
Learn more about why nation-state actors target identities, SaaS attacks, gain deeper insights, and remediation advice on our blog. Or get in touch with us to assess your environment for risks of SaaS threats.
To explore more on these types of SaaS-specific attacks, and gain deeper insights and remediation advice visit on our website.




