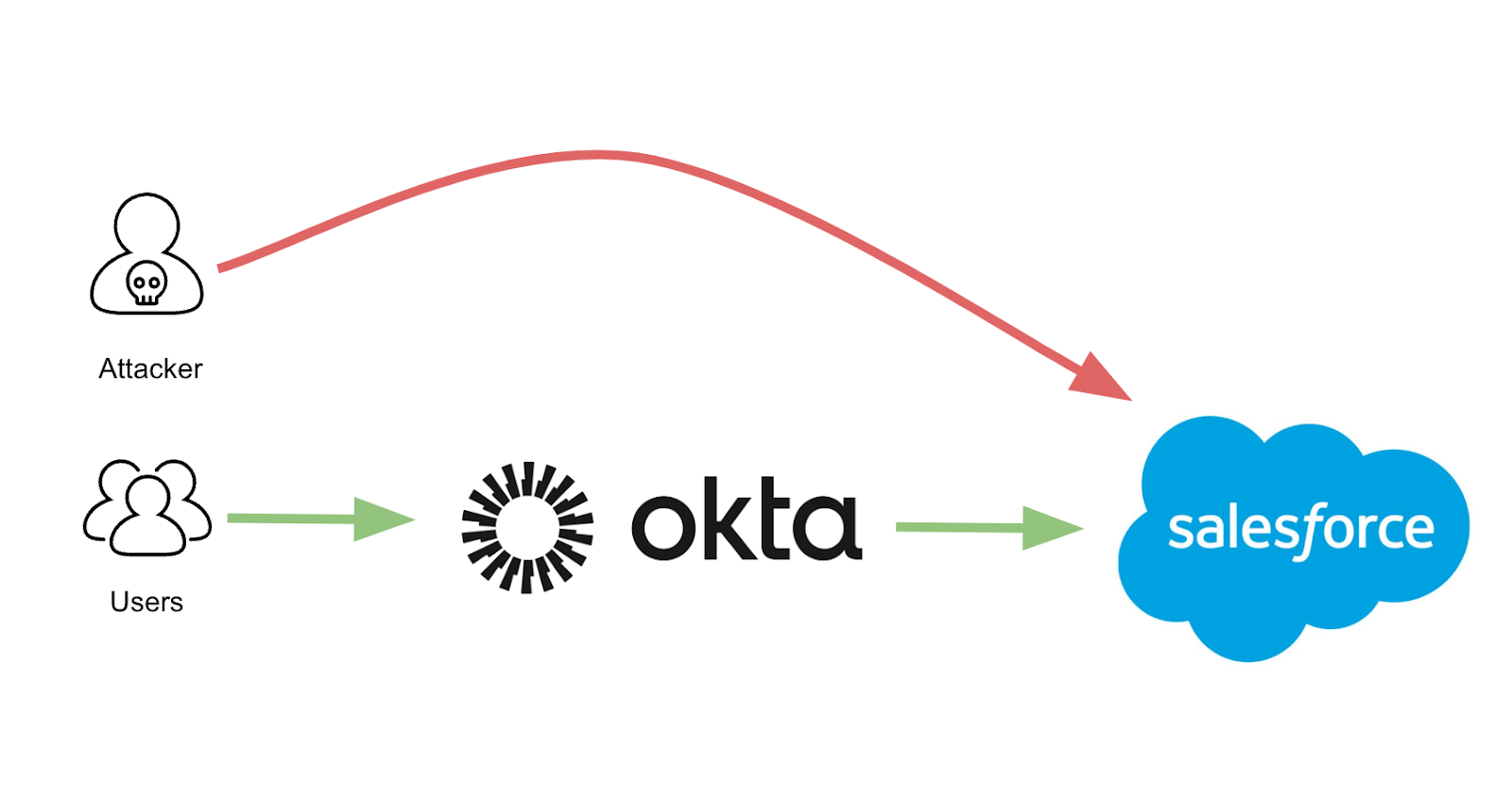
Attackers are increasingly bypassing Identity Providers (IdPs) like Okta, OneLogin, and Microsoft to gain access to Salesforce. In fact, in 2023, Salesforce was one of the six most targeted SaaS applications.
Protecting your core business operations and data requires hardening your SaaS posture and closing this loophole quickly. We expect this to be a popular attack vector in 2024.
In this blogpost, we explore:
- How attackers are able to circumvent the powerful security controls IdPs deploy and log-in to Salesforce directly
- How to federate Salesforce, and
- Proactive steps to detect similar gaps in posture and prevent attackers from bypassing the IdP
IdPs and MFA are Vulnerable to Weak Posture
Organizations are increasingly placing-critical applications behind IdPs and SSO. This creates a central point of entry to manage SaaS provisioning, life-cycle, and security. Moreover, investments in strong MFA solutions ensure these authentication mechanisms are robust against attackers.
However, this is not the full story. Our security research team found that:
- 85% of users can bypass IdPs and access apps locally
- 95% of those users are not required to complete MFA
Just enabling users to be federated through the IdP does not prevent employees—or attackers—from logging-in locally to Salesforce or other SaaS platforms using their username and password. Disabling this configuration often requires additional steps.
Let’s review how Salesforce admins can solve this issue and harden their posture.
How to Federate Salesforce in 4 Steps to Prevent Attackers from Bypassing the IdP
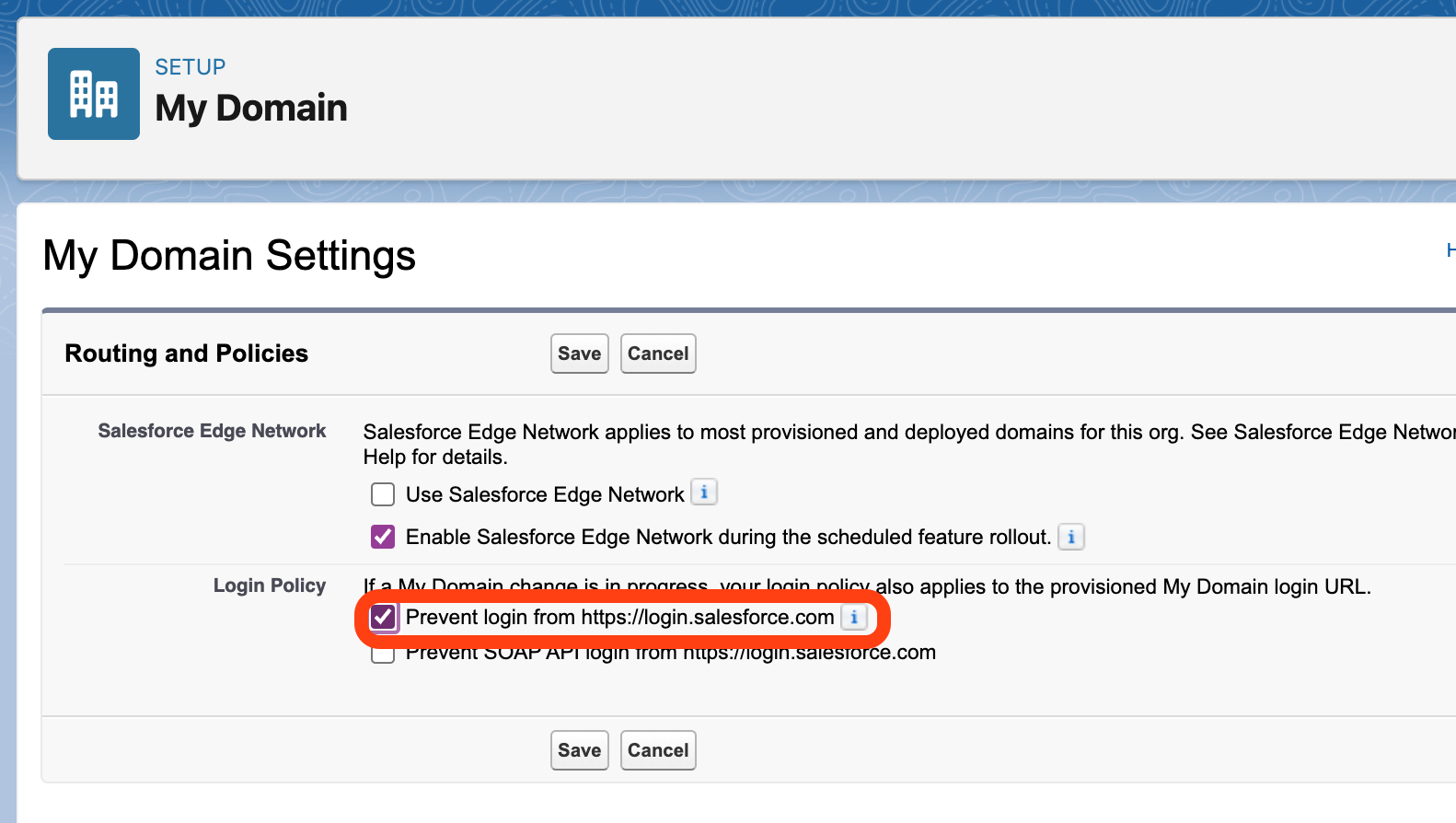
1. Disable Direct Login
From the Admin Console, click Setup and then Company Settings. Select My Domain, and choose Routing and Policies. Ensure “Prevent Login from https://login.salesforce.com” is checked.
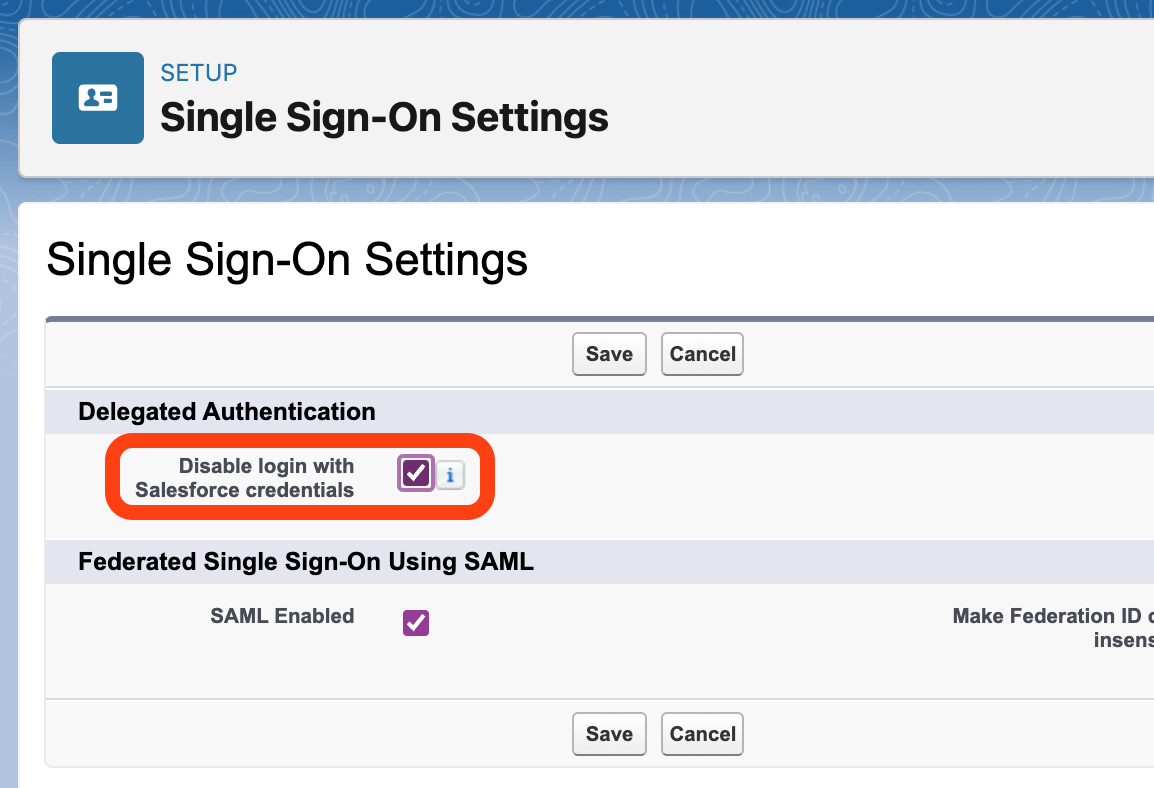
2. Disable Login Using Salesforce Credentials
Browse back to the Admin Console. Select Setup, then Single Sign-On Settings. Check that “Disable Login with Salesforce Credentials” is also selected.
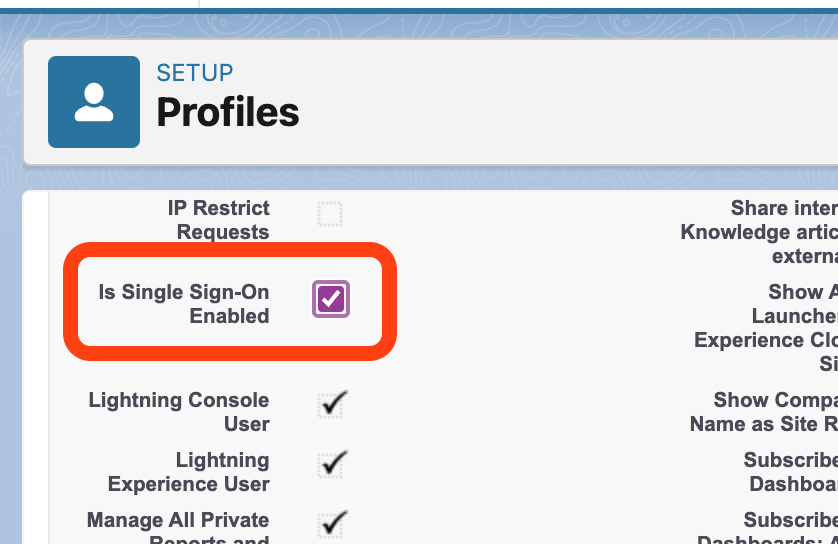
3. Enable SSO at the Profile/Permission Level
Next, admins need to federate every user. This can be done by ensuring “Is Single Sign-On Enabled” is set to true.
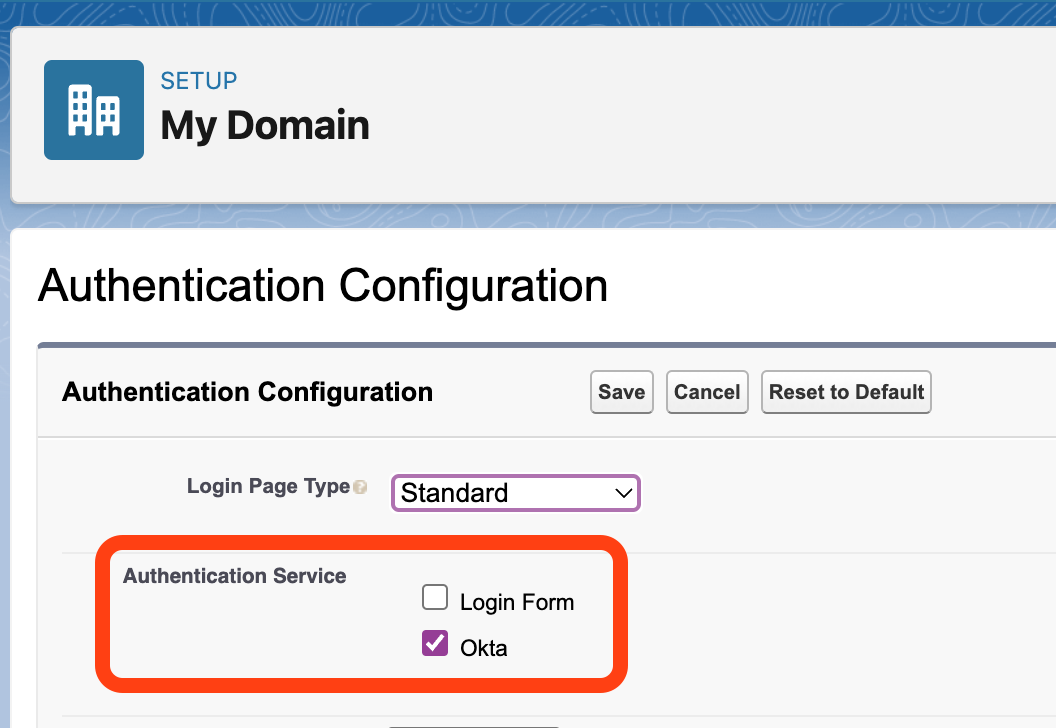
4. Make the IdP the Default Authentication Service
Finally, set the default authentication service to the chosen IdP. This ensures that users that browse directly to Salesforce are prompted to login through the IdP.
5. Test Bypassing the IdP for Yourself
To check if your Salesforce application is vulnerable, try to bypass the IdP yourself! First, browse to the Salesforce tenant. You will be directed to the default authentication service.
However, by simply appending the URL with “?login=true” at the end you can access the local login page. See the animation below:
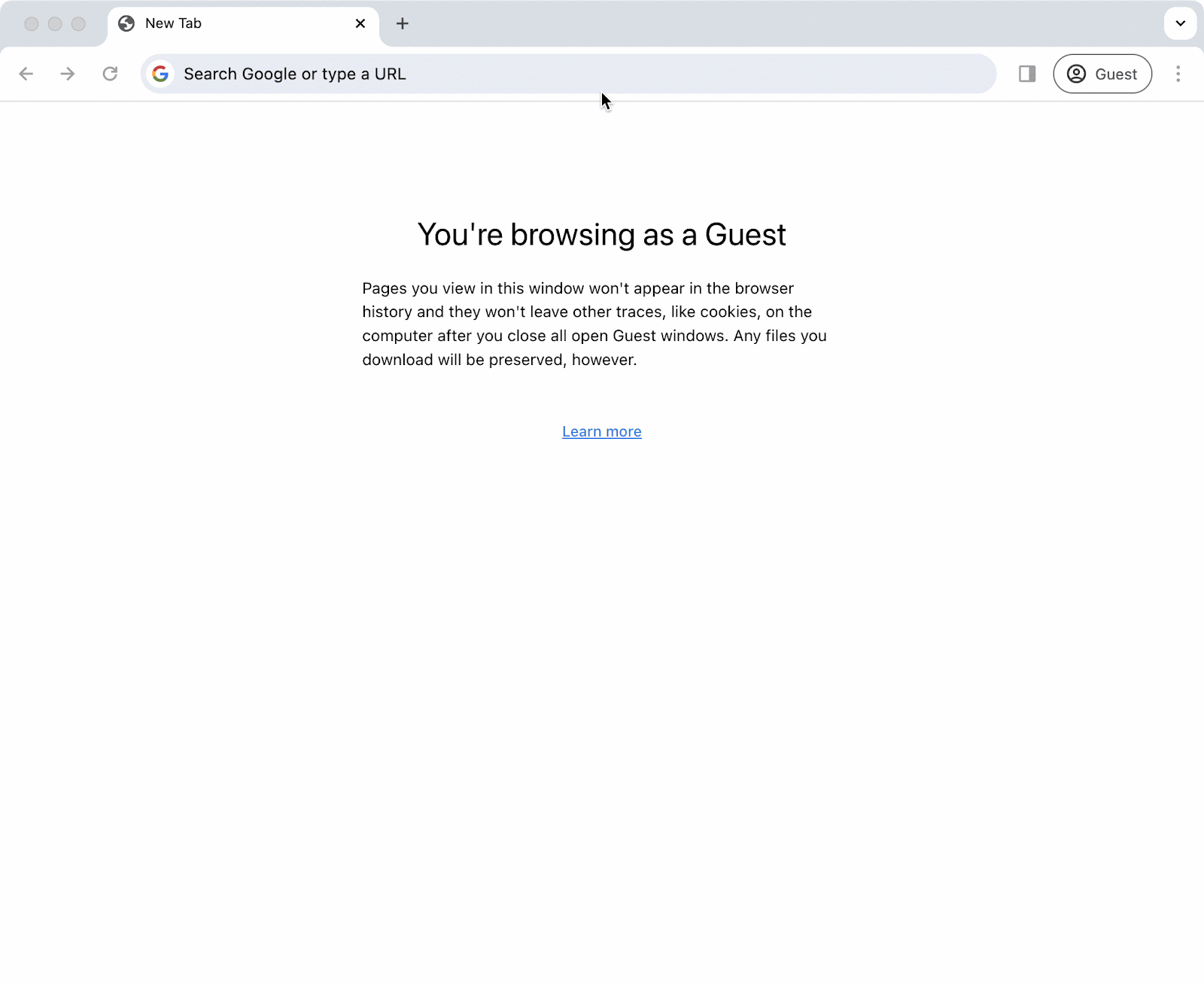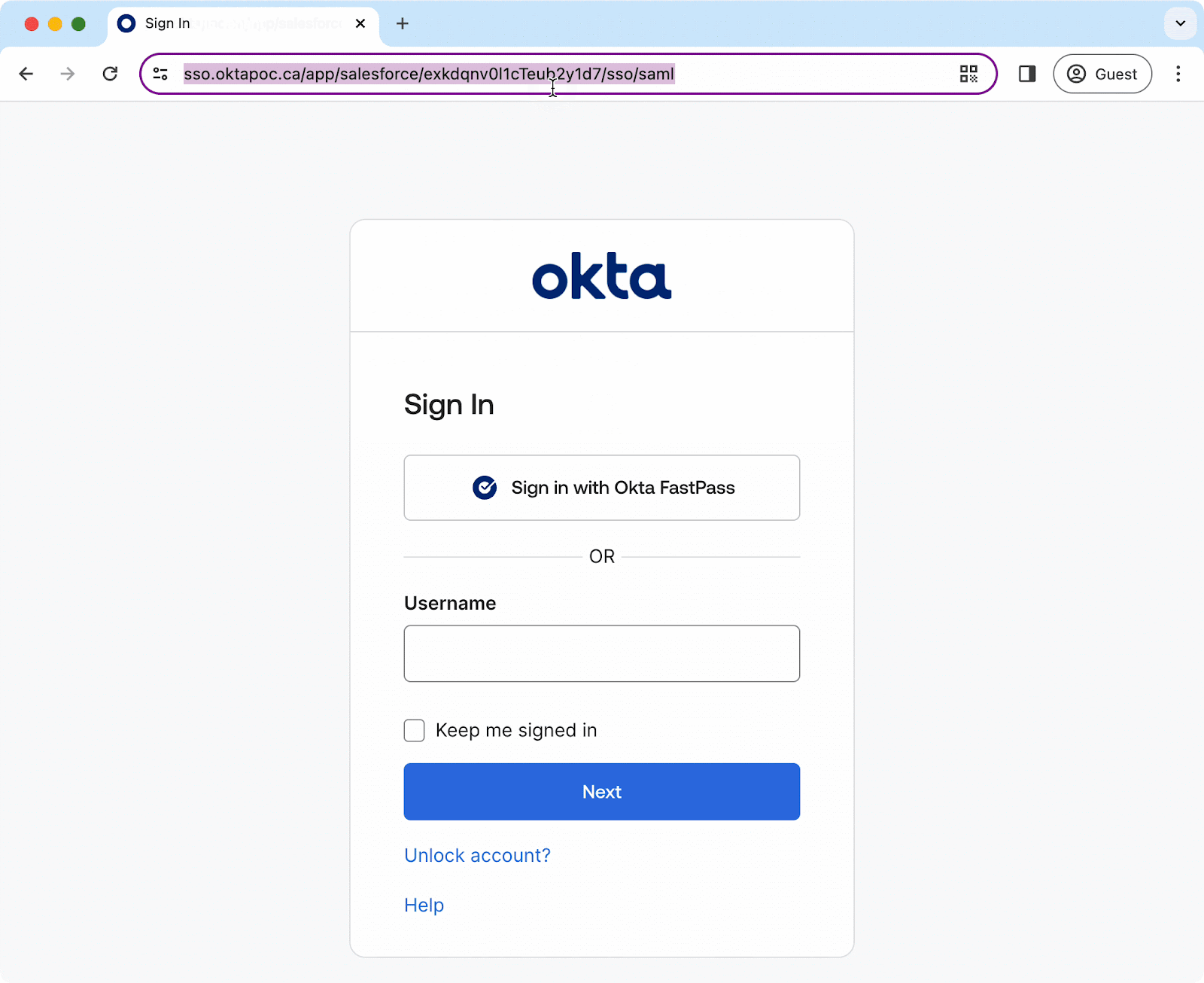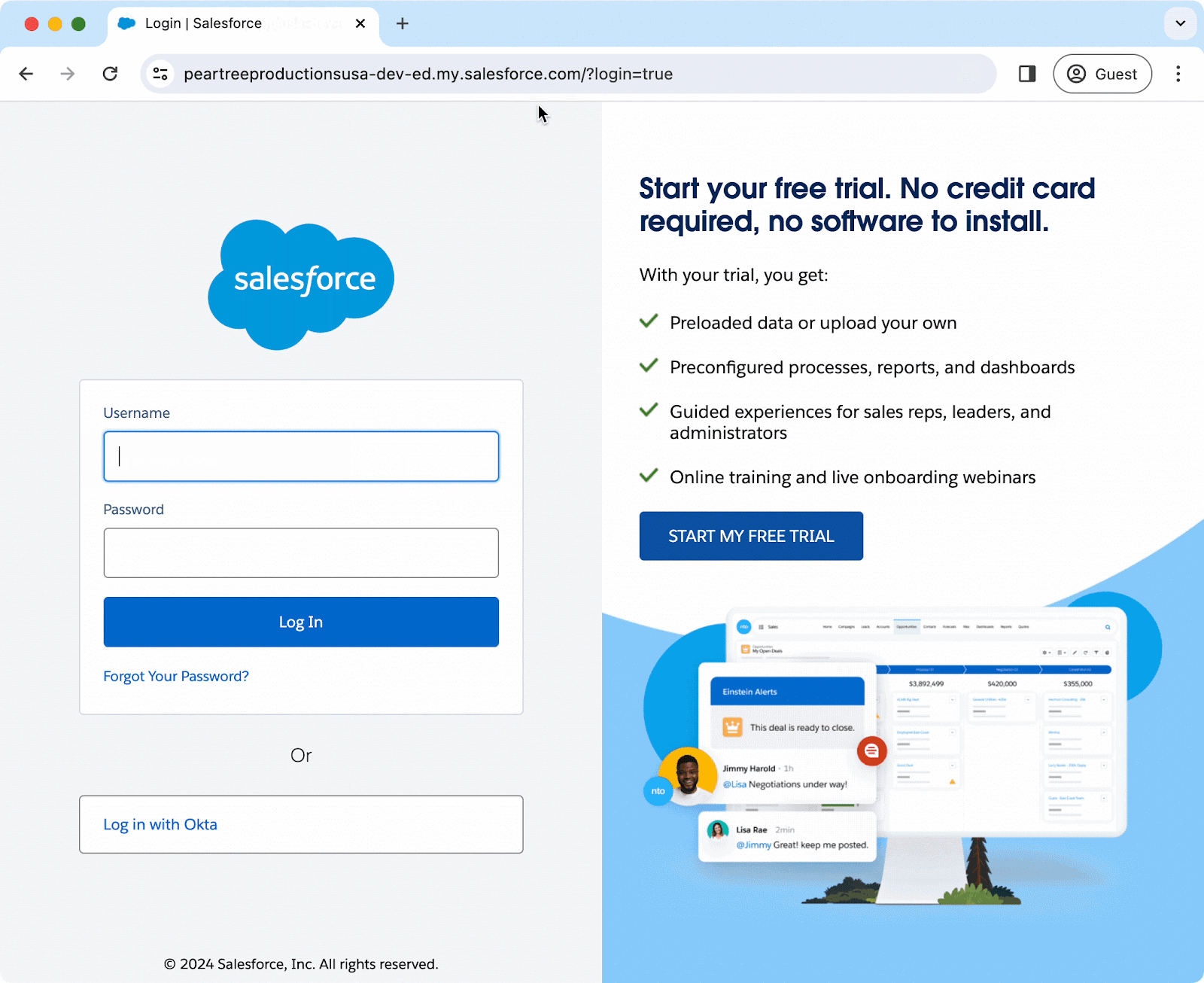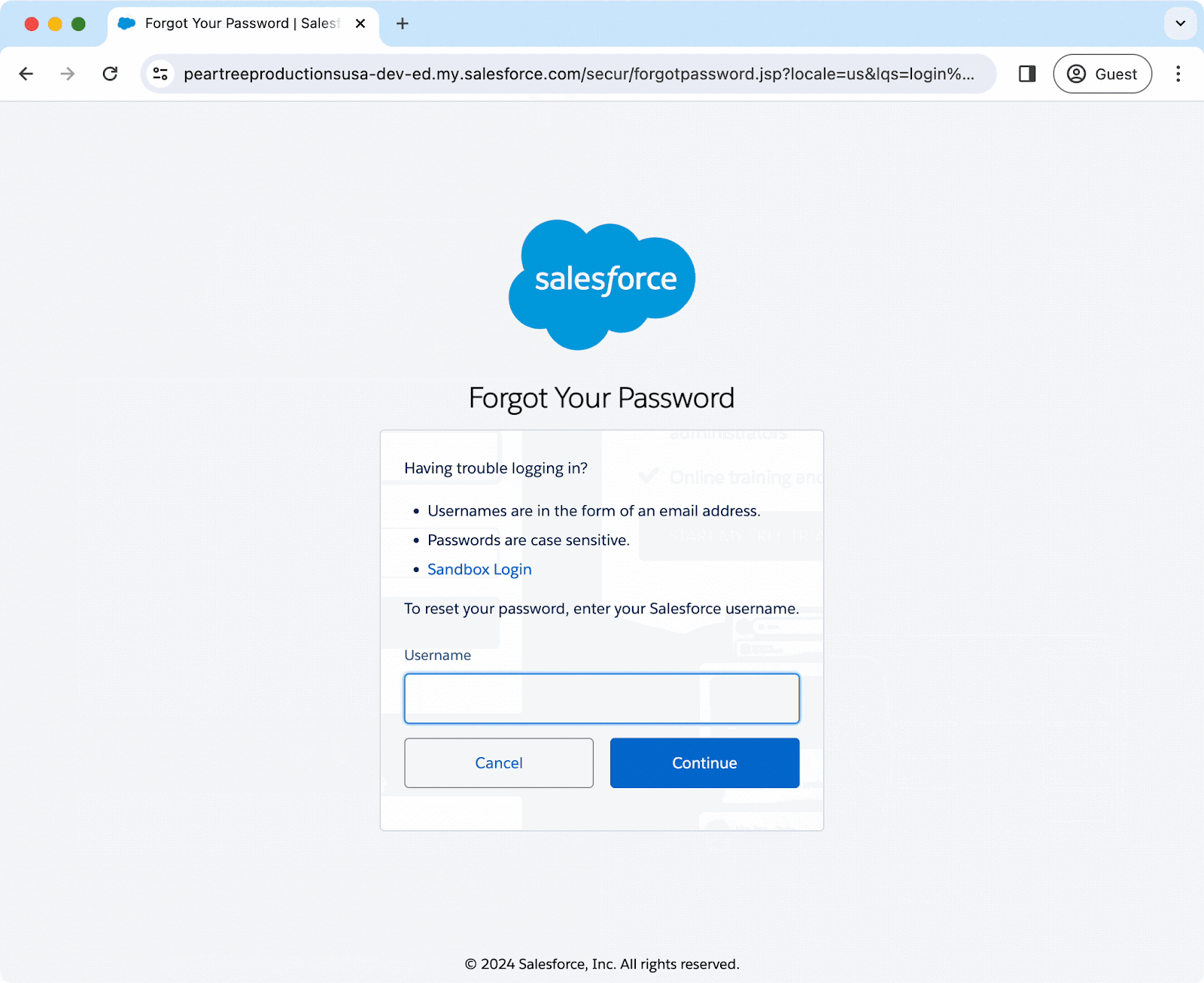
Even though the IdP removes password ownership from users, attackers can still breach the app. If they click “Forgot Your Password” and enter the username, a reset email will allow them to log in directly.
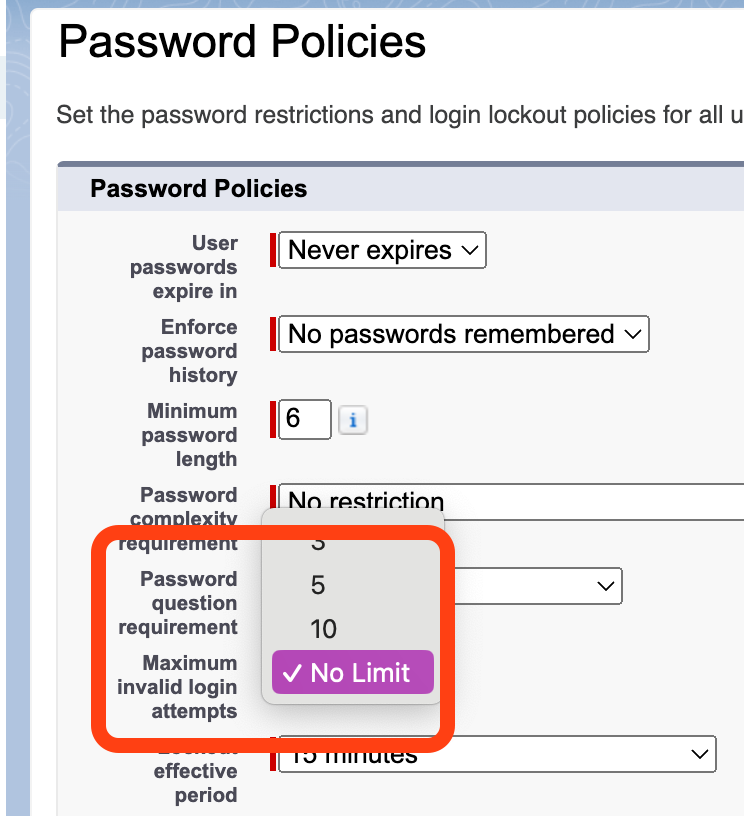
The strength of your password policy—often weaker than that of the IdP—can determine if a brute force attack succeeds, especially without limits on login attempts.
A Growing Problem
This misconfiguration frequently occurs in Salesforce, and it’s even more prevalent in other applications. As defenders strengthen the IdP, attackers seek new ways to undermine it.
Implementing the proactive steps mentioned is one strategy to reduce this vulnerability in your SaaS applications. For instance, review the settings mentioned above for all users (excluding administrators) for every Salesforce tenant you manage.
Yet, can you effectively manage your SaaS posture manually for every app?
Prevent Attackers from Bypassing the IdP with Obsidian Security
Automating this process through a SaaS security platform ensures organizations always harden their posture. It is crucial for any organization relying on SaaS applications to have alerts in place to verify the correct implementation of posture and security tools.
Pro tip: Obsidian Security frequently observes this issue across various SaaS applications, not just Salesforce. Many application owners lack the background or experience to consistently adopt an adversarial mindset. Implementing tools that alert IT teams to opportunities for posture hardening promotes better identity security practices.
Visit the Obsidian Security website to learn more about our proactive alerts and preventative controls to block attackers before they breach.




