The December 2024 Chrome Extension Breach
In the last week of 2024, Cyberhaven experienced a huge supply chain attack. After gaining initial access through phishing, cybercriminals published a malicious version of the Cyberhaven Chrome extension. This extension passed Chrome Web Store’s own security review, and contained code capable of exfiltrating cookies, session tokens, and other sensitive data from users.
Cyberhaven wasn’t the only one—this attack was part of a broader campaign targeting at least 35 Chrome extensions. Overall, it affected 2.6 million users. At Obsidian, we learned about this attack from the news and from one of our customers. This customer had downloaded the malicious extension, but thanks to an alert from Obsidian, they were able to quickly take action and remove it.
Why Employees Use Risky Browser Extensions
Browsers have become the gateways to work. They’re the most used desktop applications, connecting us with all the SaaS apps that run our day-to-day. And just like with SaaS, employees often install and use browser extensions to make their work run faster (or just for fun). This includes ad blockers, security tools, productivity enhancers, and even shopping assistants. Employees will customize their browser with a whole suite of extensions. IT and security teams already lack visibility into the SaaS apps their users are deploying, and browser extensions are one level worse.
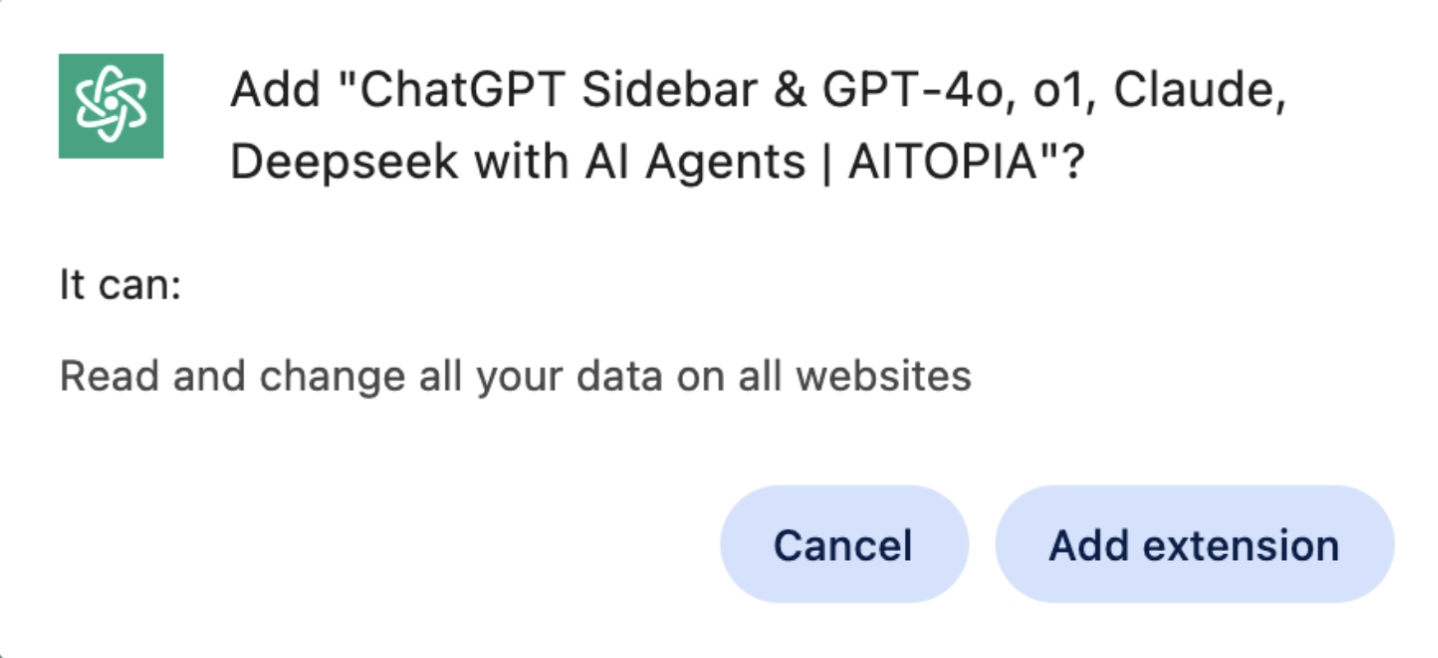
Even without an attacker in the picture, employees can grant risky permissions to browser extensions, like in the example below.
How Threat Actors Weaponize Browser Extensions
Attackers weaponize browser extensions in a few different ways.
One common tactic is listing malicious extensions on reputable browser stores. This is what happened with Cyberhaven. Because users are downloading an extension from an established brand name like Google, they believe they’re safe. But attackers can sneak their extensions past security checks by mimicking well-known vendors or claiming that their extensions serve popular purposes.
Threat actors will also purchase or take over previously legitimate browser extensions. Once in their ownership, they begin to push out malicious updates. In this situation, it doesn’t matter if your browser extensions were originally safe and authentic! Attackers can still get in.
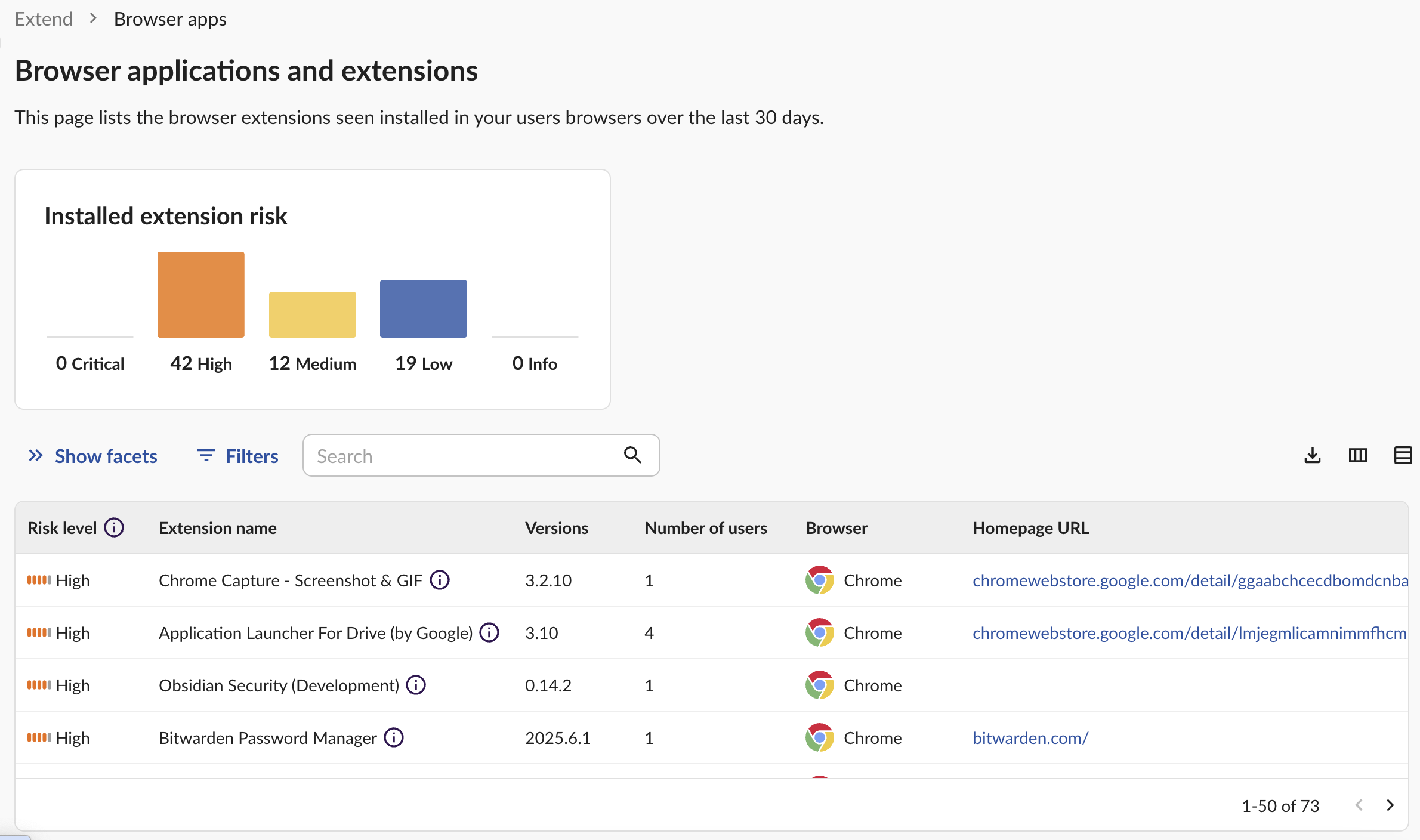
Detecting & Prioritizing Malicious Extensions with Obsidian
This might as well be our official mantra by now, but as with other security challenges, the first step is visibility, visibility, visibility. It’s important to get a thorough catalogue of all browser extensions sitting in your environment as you think about addressing this challenge.
Traditional app discovery tools often sit in inboxes to detect when users sign up for new apps. However, browser extensions don’t generate email notifications or other external signals. They only leave traces within the browser itself. That’s why Obsidian operates at the browser level too.
Use Obsidian Security to sort all discovered browser extensions by risk level, permissions, and number of users, among other filters, so you can easily prioritize which extensions to chase down first. Start with a free trial today.