Critical data has migrated to SaaS, and attackers are taking advantage of this new avenue for exploitation—monthly SaaS breaches are up 300% year over year. Due to the critical role SaaS applications play in delivering essential services, every hour of downtime can cost millions. New security policies are needed to address this blindspot.
Two recent European regulations, the second Network and Information Security Directive (NIS2) and the Digital Operations Resilience Act(DORA), increase SaaS cybersecurity compliance requirements by making scoped entities responsible for the security of their applications, SaaS identities, and data.
Adapting to this new reality requires a comprehensive understanding of your SaaS ecosystem. Every shadow SaaS application or unknown integration adds risk and affects compliance. This blog will summarize the key principles relevant to SaaS for NIS2 and DORA, plus provide guidance on how organizations should prepare.
What’s New in NIS2?
NIS2 applies to public and private sector entities that provide critical services or infrastructure within the EU. The updated directive now defines two new classifications, “Essential Entities” and “Important Entities,” each with modified cybersecurity obligations. Entities must adhere to controls related to risk management, reporting of cyber incidents, and information sharing. Covered entities will need to implement new processes and policies to comply by October 2024.
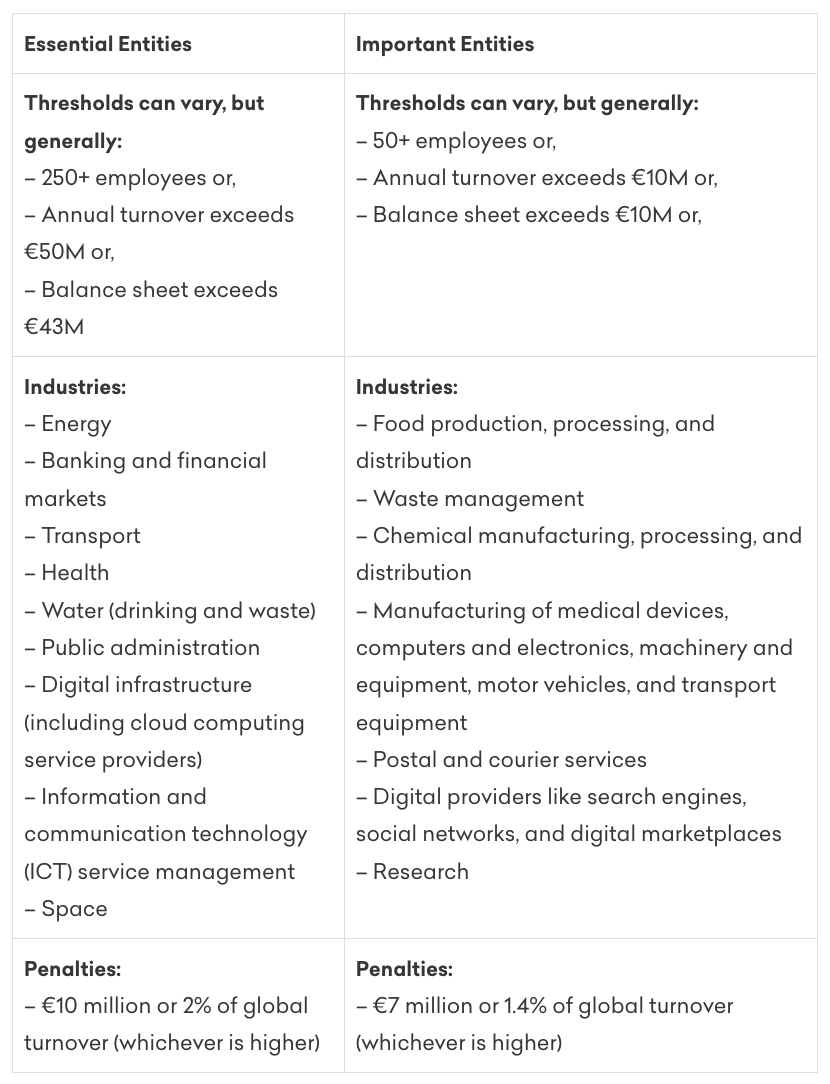
Mid-sized entities (below the Essential size thresholds) within the Essential industries are classified as Important unless otherwise stated by the member state; some exceptions ensure certain industries are always classified as Essential, such as DNS service providers, regardless of size.
Additionally, NIS2 introduces personal liability for management. Penalties could be a ban from holding management positions in the case of repeated violations.
Failing to meet NIS2 is not an option—between the millions in fines and personal liability, there is too much on the line.
What Is DORA and How Is It Different from NIS2?
Taking effect in 2025, DORA introduces a strong cybersecurity mandate for European financial entities, as well as critical third-party ICT service providers that support them. In the case of a firm falling under both NIS2 and DORA, DORA takes precedence; however the two pieces of legislation are designed to complement, rather than override each other. While NIS2 has specific fines, DORA leaves the assessment of sanctions to member states and appropriate authorities.
Similar to NIS2, DORA introduces strict guidelines for incident reporting, resilience testing, third-party risk, and risk management. DORA also directs entities to have threat detection mechanisms in place for ICT network performance issues and ICT-related incidents, and to identify potential material single points of failure.
Specific to the UK: Due to Brexit, NIS2 and DORA do not automatically apply to the United Kingdom, however any firm that provides relevant services to scoped entities will be indirectly impacted and must meet certain compliance regulations.
NIS2 and DORA Technical and Organizational Measures

For a more thorough review of relevant guidelines and how to meet the new compliance requirements, download our white paper.
Streamline SaaS Compliance with Obsidian Security
NIS2 and DORA introduce a robust set of controls for entities to adopt specific to their applications, SaaS identities, and data. The challenge is that companies often have hundreds of apps; and critical SaaS, such as Salesforce, could include dozens of individual instances.
Relying on a manual approach to meet the requirements for NIS2 and DORA is not scalable. Creating a mapping framework with a SaaS security solution automates the process to ensure continuous compliance.
Map App Configurations to NIS2 and DORA
Ensuring each app is properly configured to controls like MFA and encryption is difficult—it takes 28 days on average to audit an individual SaaS app. Plus, teams must monitor apps over time to combat configuration drift.
The Obsidian platform quickly and continuously surfaces all apps in your environment and measures how they perform against the internal or external compliance standards you follow. Monitoring your posture with Obsidian gives security teams the ability to rapidly assess app configurations and remediate any risk.
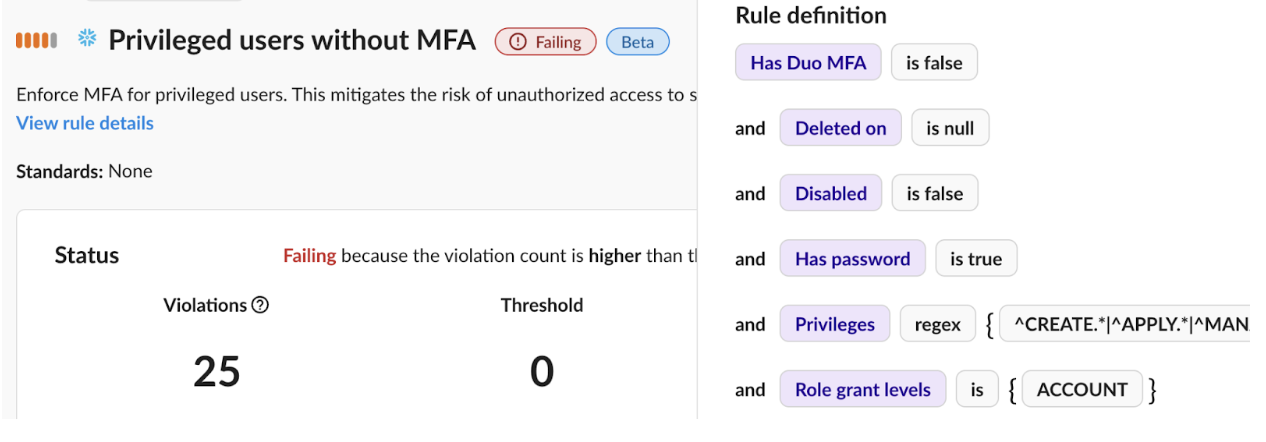
Ensure Resiliency
Beyond posture, NIS2 and DORA specifically call out operational resiliency as a core component. The best way to get ahead of this compliance mandate is to implement robust identity security measures to prevent compromises—most cyberattacks target identities. Protecting your SaaS identities is a critical component of compliance for NIS2 and DORA.
Obsidian’s platform deploys ML-based algorithms to identify anomalous user behavior and stop threats in minutes.
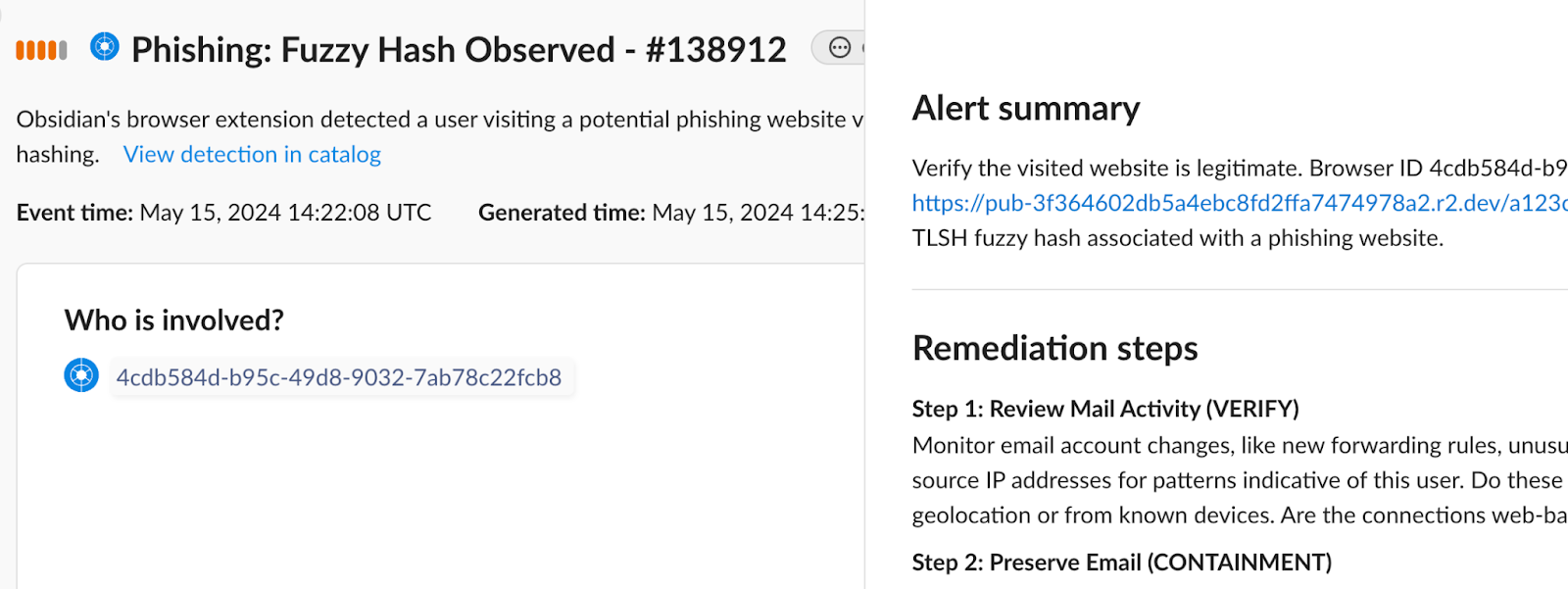
Threat Detection
The need to promptly detect anomalous activities is specified in DORA, but will also help ensure resiliency for NIS2 by preventing attacks from impacting operations or exfiltrating data. Obsidian Security uses ML-based algorithms, along with out-of-the-box detection rules informed by insights from the largest repository of SaaS breach data, to identify anomalous behavior and stop attack vectors like AiTM, SIM swapping, and help desk social engineering before data loss.
Control Data Access
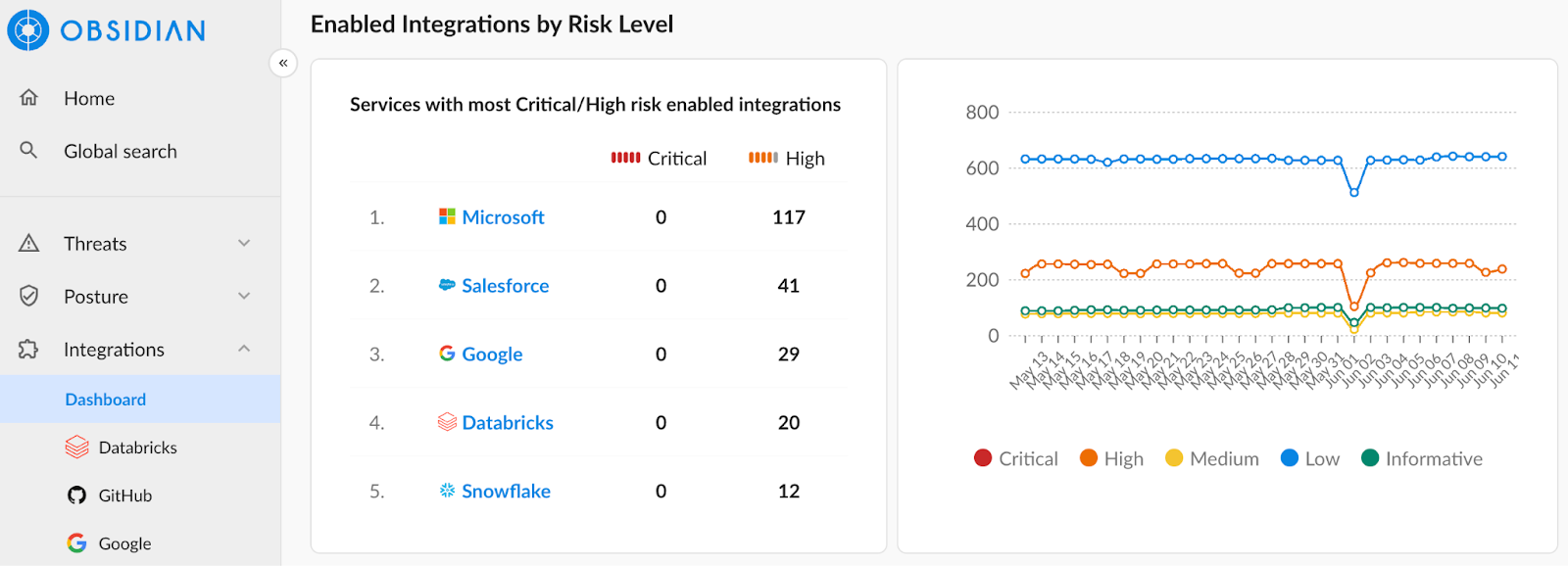
Lastly, data governance is especially challenging across SaaS. Ensuring proper privileges, access, and integrations across known applications alone is complicated, but every shadow SaaS app or hidden integration impacts your risk profile.
With Obsidian, security teams are able to understand data flows between apps to know how data is accessed and keep it secure. Partnering with platforms like Snowflake and Databricks ensures your data is properly controlled across its journey from application to application.
Conclusion
Obsidian Security streamlines compliance for NIS2 and DORA by combining application posture with identity and data security to prevent all types of SaaS breaches. For a more detailed understanding on how the Obsidian Security platform can automate your SaaS compliance for NIS2, DORA, read our white paper or schedule a demo.




