The zero trust odyssey
It’s been over a decade since former Forrester analyst John Kindervag helped popularize the term “zero trust,” and while the underlying principles aren’t new, the model of “never trust, always verify” has never been more relevant. In response to an increasingly mobile workforce and the widespread adoption of cloud services, zero trust has helped enterprise security evolve from a fortress mindset (perimeter security) to a more thoughtful identity-centric model. Just as the framework is able to evolve with changes in how companies connect, access, and use corporate IT, security teams recognize that the journey to “never trust, always verify” is continuous.
Bringing the principles of zero trust to SaaS
Zero trust brings substantial security advantages to an enterprise, as avoiding implicit trust minimizes the likelihood, impact, and time to detect a breach. Zero trust requires the implementation of three key tenets, as defined by National Institute of Standards and Technology (NIST 800-207):
- Continuous verification of access for every element
- Limiting the impact of a potential breach
- Collection of behavioral data to facilitate faster incident response
While these principles can be applied to infrastructure in the data center or cloud with relative ease using well-established techniques, the tools and processes are not well known or repeatable for SaaS. As a practical stopgap, most companies rely on single sign-on (SSO) and multi-factor authentication (MFA) as their primary enforcement mechanism of their zero trust architecture for SaaS. This allows companies to provide some verification of access for users but fails to verify all elements in the SaaS environment. For those companies, zero trust stops at the identity provider and leaves SaaS applications out of scope. Security teams are unable to detect attackers that breach or bypass the identity provider and could otherwise go undetected, including cookie stealing, OAuth abuse of third-party apps, insider threats, and non-user accounts.
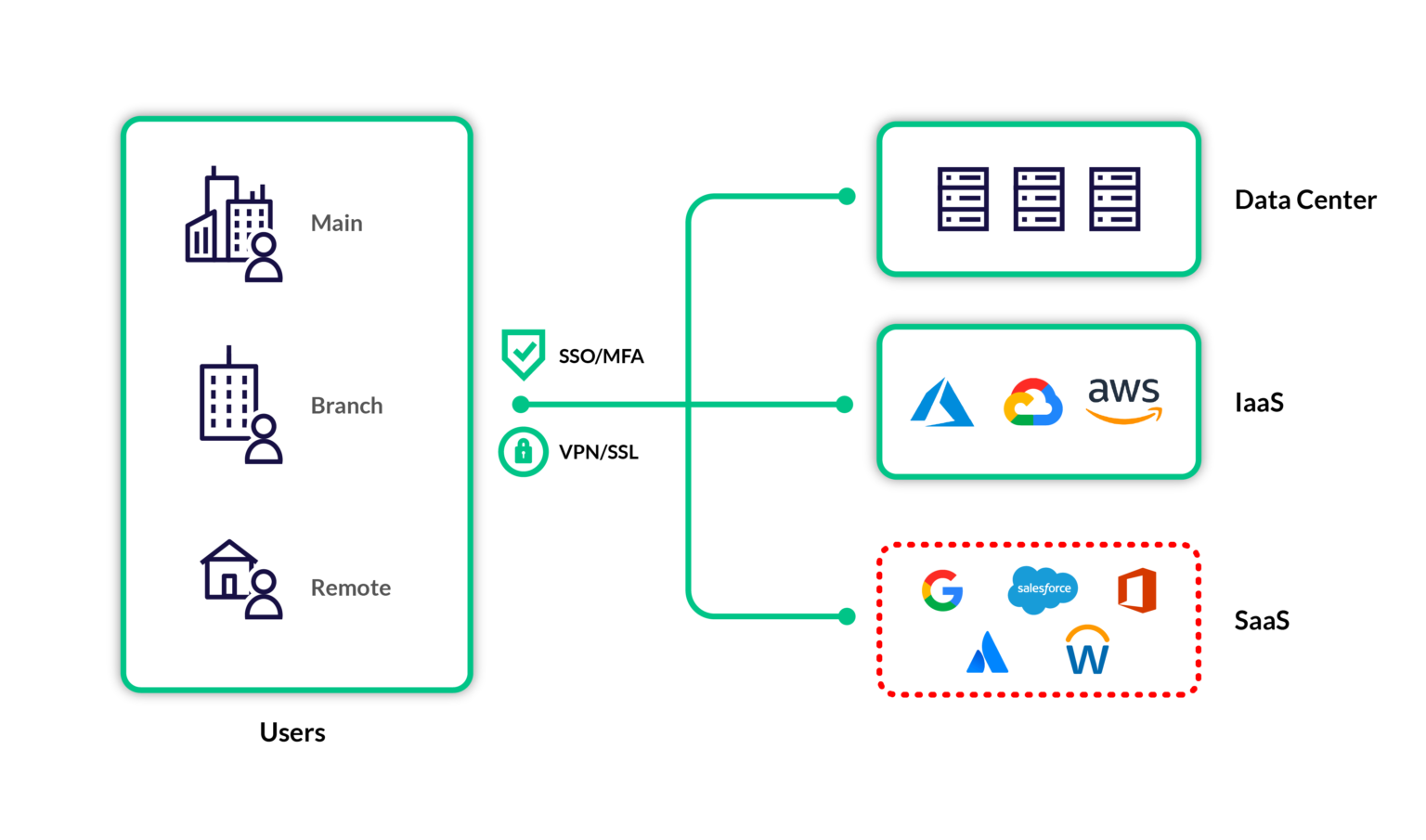
Zero trust for SaaS requires a deeper understanding of each application, not relying on the identity provider alone. As risk can come from the client connections, applications, and integrations of cloud-based services, your security team needs holistic coverage of these core SaaS components in order to extend the principles of zero trust.
The Obsidian approach to zero trust
Obsidian provides comprehensive security and compliance for SaaS built on a deep, consolidated understanding of your business-critical applications—making Obsidian the first truly zero trust solution for SaaS.
Our approach is built on a foundational knowledge graph populated by data on the users, configurations, privileges, and activities within and across your applications — including your identity provider. Obsidian’s threat mitigation and posture management solution extends the three tenets of the zero trust framework to the components within your SaaS environment:
- Obsidian continuously verifies connections to your SaaS applications not only from users, but also from OAuth and other connected applications to detect breaches regardless of where they originate.
- Obsidian delivers configuration hardening recommendations to reduce the likelihood of a breach, privilege right-sizing recommendations to minimize the impact of a breach, and advanced threat detections driven by machine learning to facilitate faster mitigation of a breach.
- Obsidian is the only true behavioral collection solution for SaaS, using a comprehensive understanding of your applications to consolidate information on configurations, accounts, privileges, and activities that inform your response to threats and posture.
These capabilities are essential to understanding enterprise risk and protecting your SaaS environment. Without them, your security team is effectively blind to threats and posture gaps within your core applications, leaving your zero trust architecture incomplete. To learn more about how Obsidian helps extend zero trust to SaaS, download our solution brief.




