Recently, we detected a phishing attack targeting one of our customers. In this blog post, we analyze the attack’s life cycle to show why you need a thoughtful solution to defend against sophisticated identity threats.
What Happened?
In a customer environment testing Obsidian’s browser extension, we observed two critical alerts triggered by the same user identity:
- Phishing Attempt: Flagged by our browser extension.
- Account Takeover Attempt: Detected within a minute by our threat intelligence system.

After investigating the user’s activity timeline, here’s how the attack unfolded:
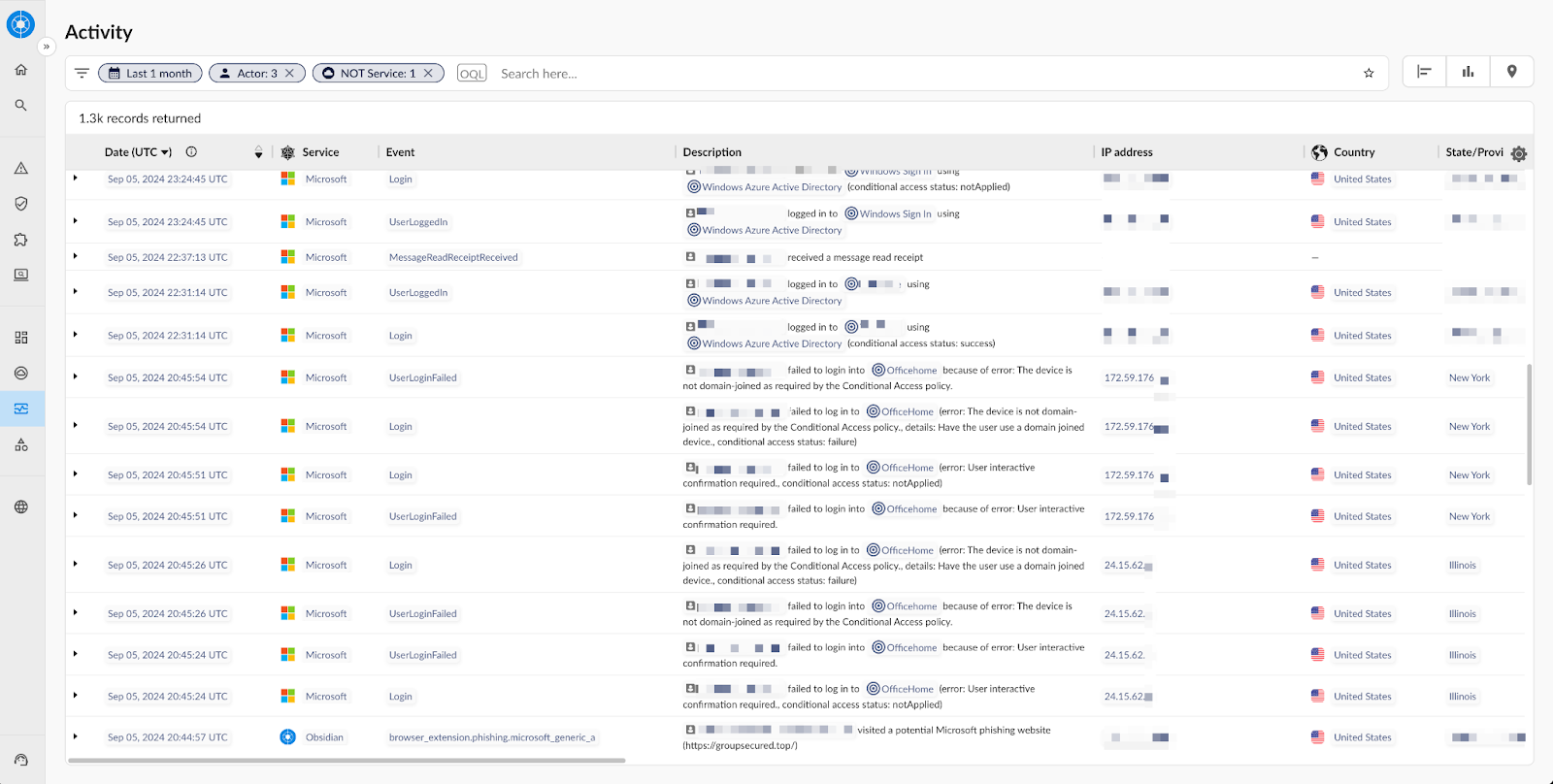
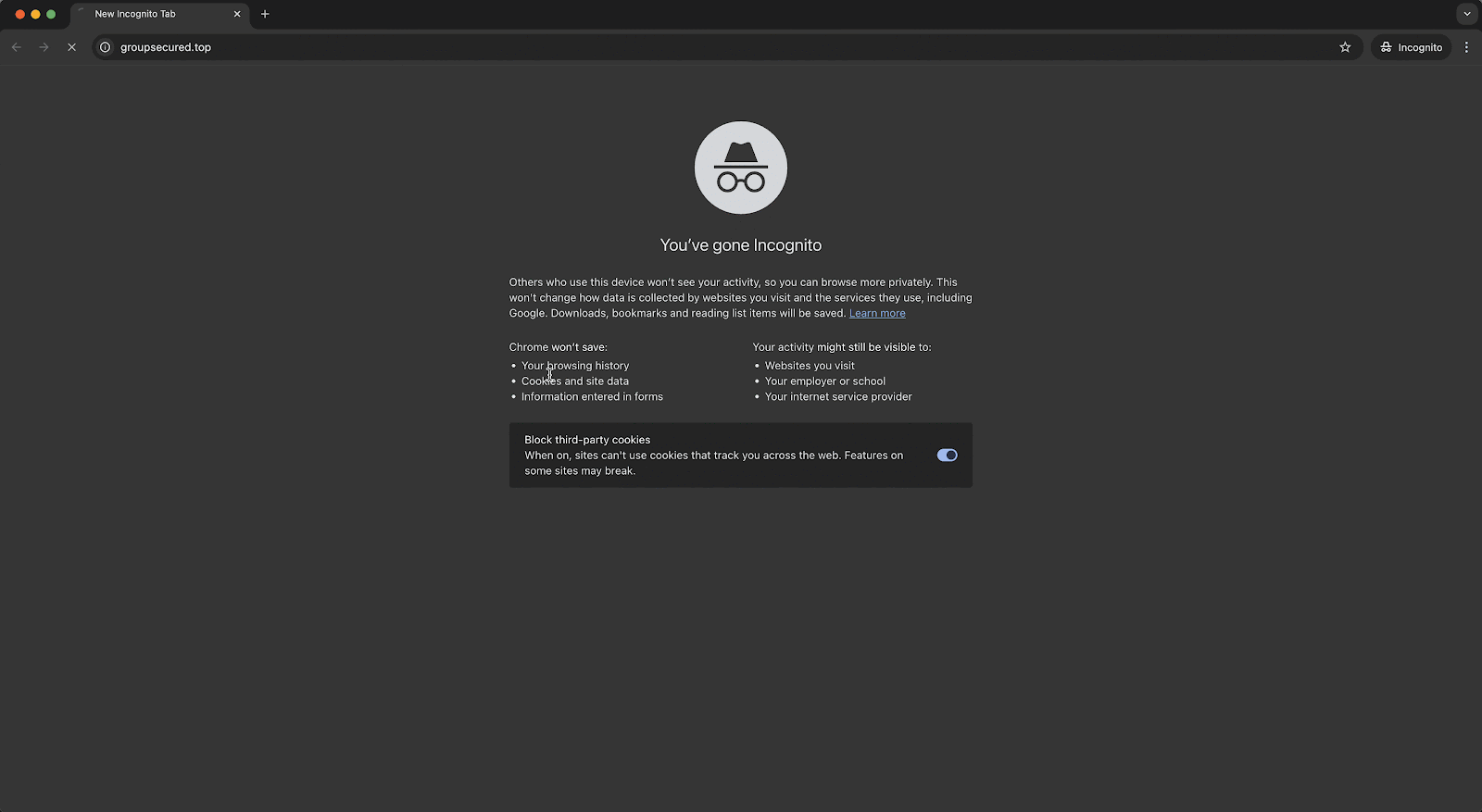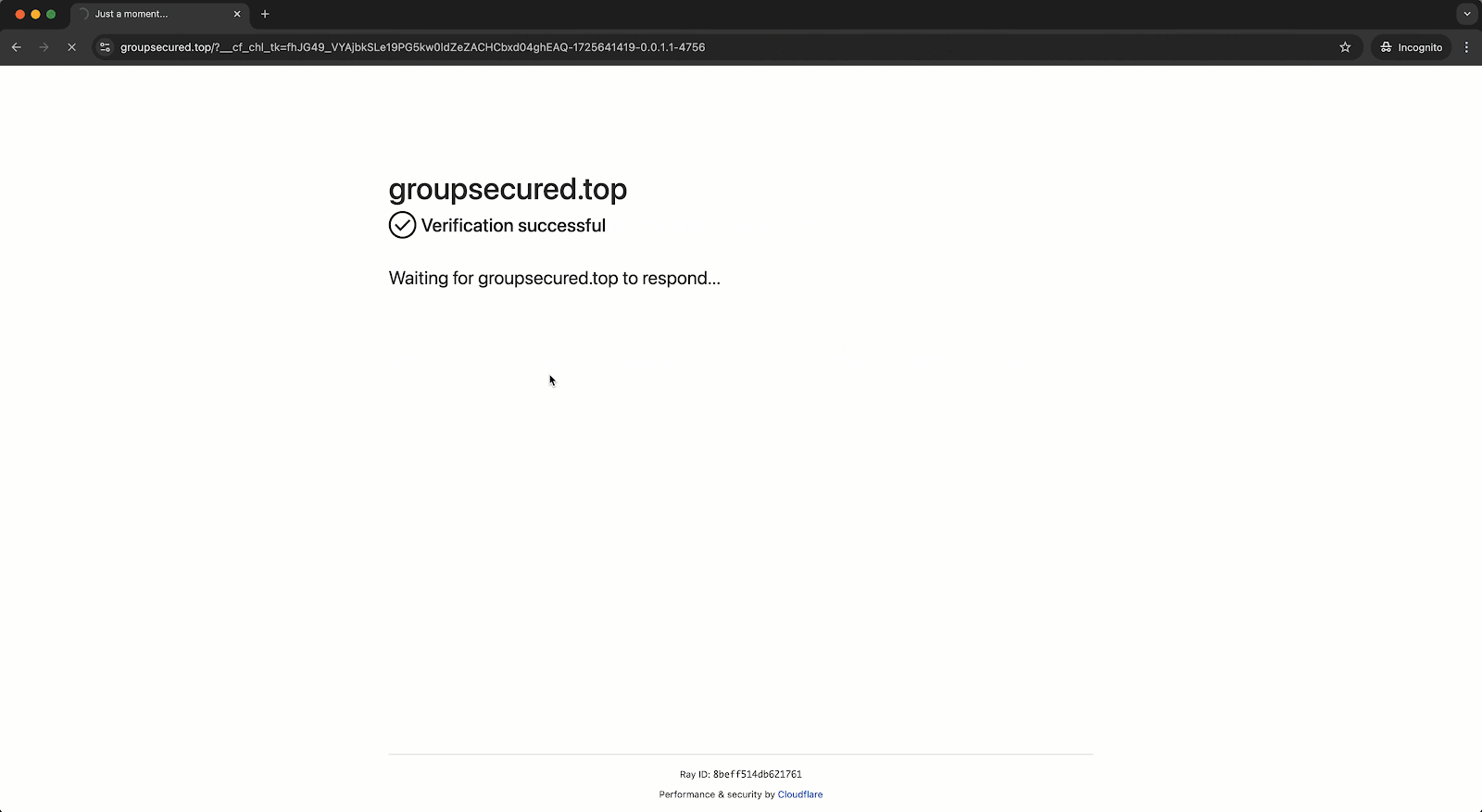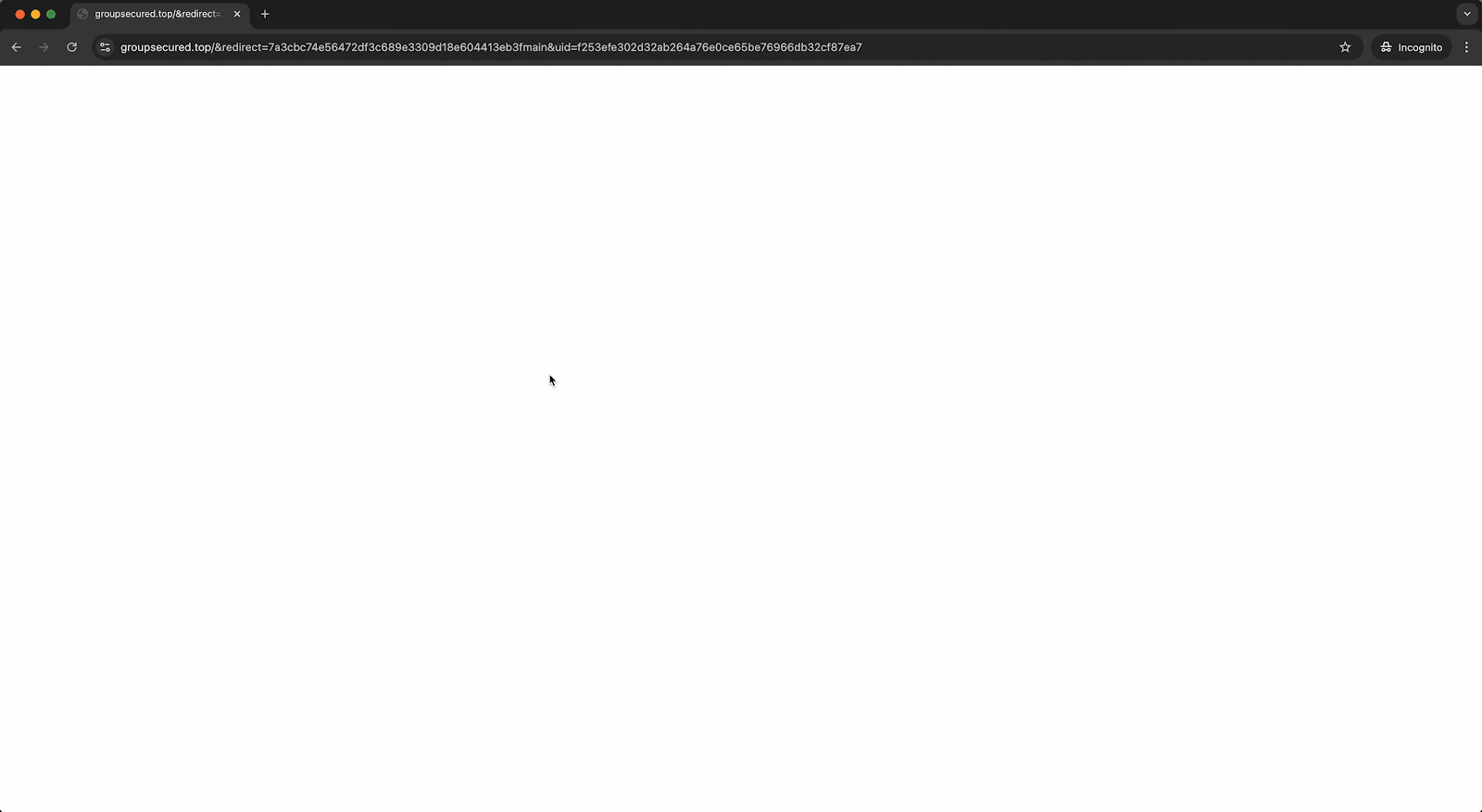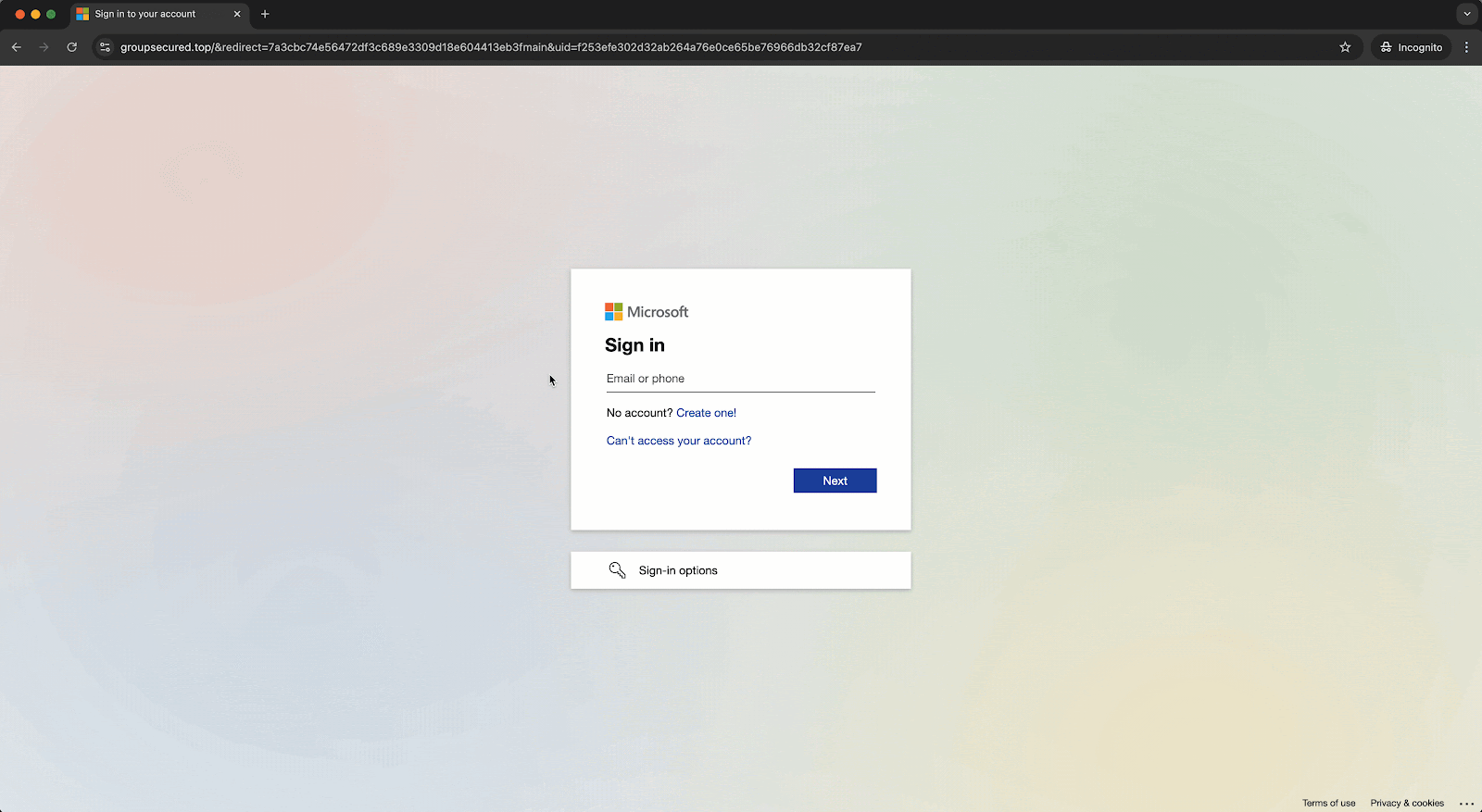
- The user accessed a phishing site: https://groupsecured[.]top/, which was flagged as malicious by Obsidian’s browser extension. However, since the extension was running in dry-run mode during the pilot, the site wasn’t blocked, allowing the attack to proceed.
- Within a minute, the attacker attempted to log in to the user’s Microsoft account via an adversary-in-the-middle (AiTM) proxy, using residential proxy IPs. Fortunately, a conditional access policy blocked the login attempt. Despite this, the user’s password was compromised, exposing other SaaS applications to future attacks. Obsidian flagged this password exposure.
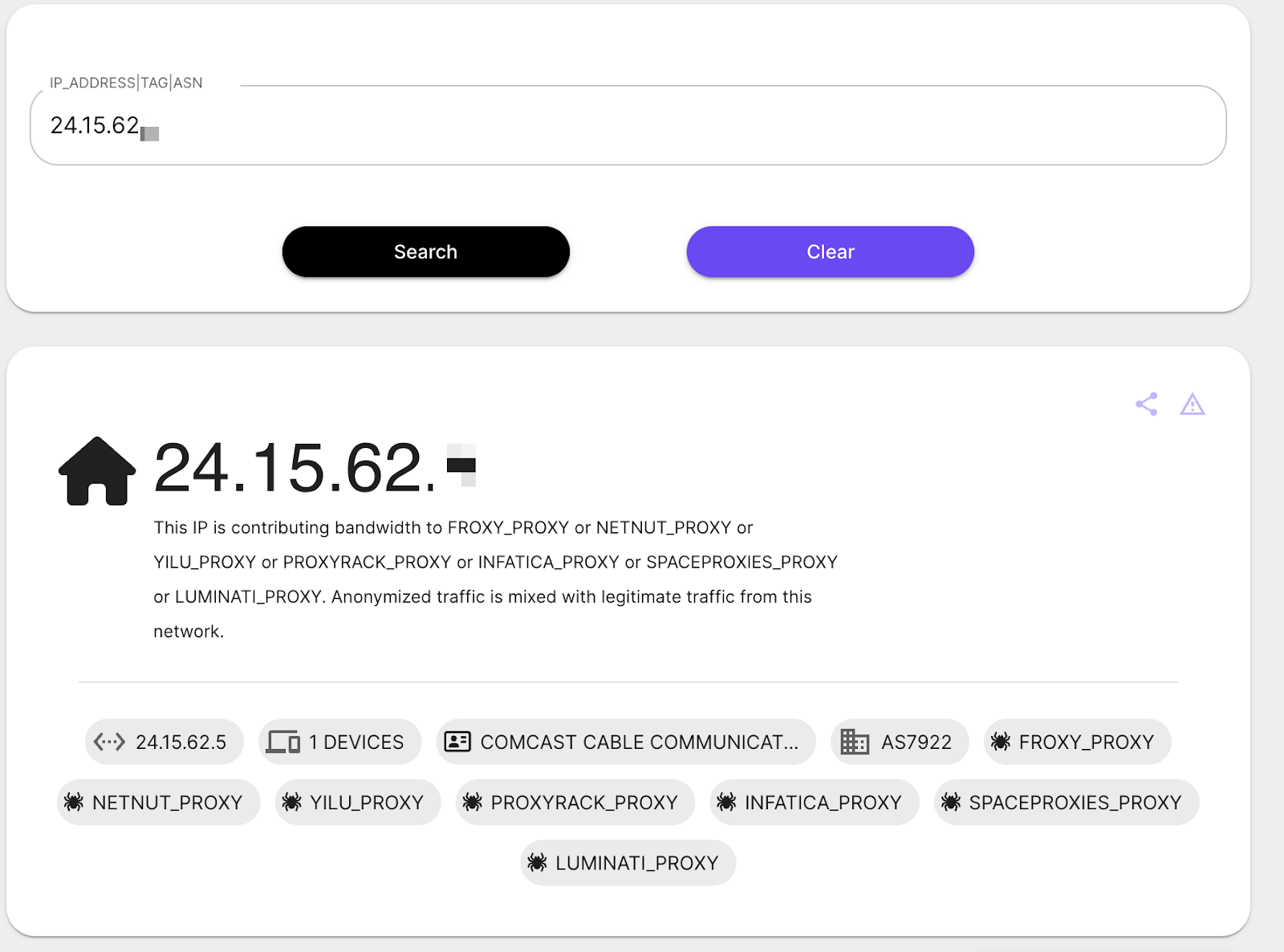
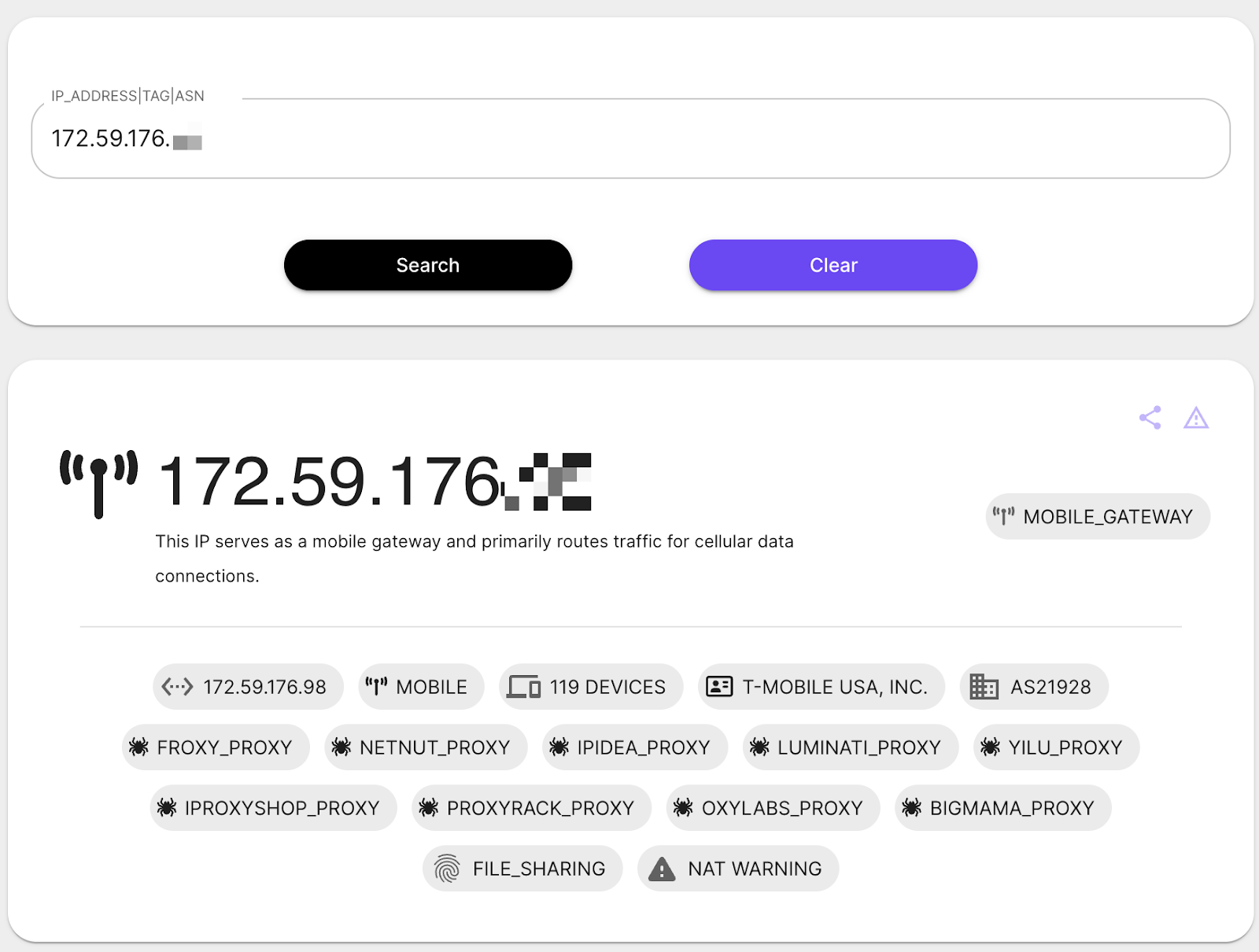
Upon closer inspection, we discovered the phishing site used Cloudflare turnstiles to evade traditional detection methods. Despite the customer having an email security gateway (ESG) in place, it failed to catch the attack.
Life of a Phish
While this might seem like a routine phishing attempt, it underscores the complexity of modern phishing techniques. Successful attacks navigate multiple layers of an organization’s defenses across the tech stacks.
A Typical Phishing Path
Here’s a simplified view of the phishing attack:

- Phishing email delivered to corporate email address
- User visits phishing site from a browser on a corporate device.
- Login credentials are stolen through AiTM techniques, and further attacks on SaaS applications are attempted.
Traditional defenses like email security filters can only go so far. As attackers evolve, they use techniques like CAPTCHA to bypass these defenses.
Alternate Attack Pathways
While the example above focuses on email-based phishing, attackers often employ alternative methods to circumvent corporate security:
- Personal email: Phishing emails are sent to personal accounts to avoid corporate email filters.

- Smishing (SMS phishing): Phishing links are delivered via text messages, especially when attackers have access to personal numbers.

These methods are frequently used in targeted attacks, exploiting personal information readily available online.
Securing the Stack
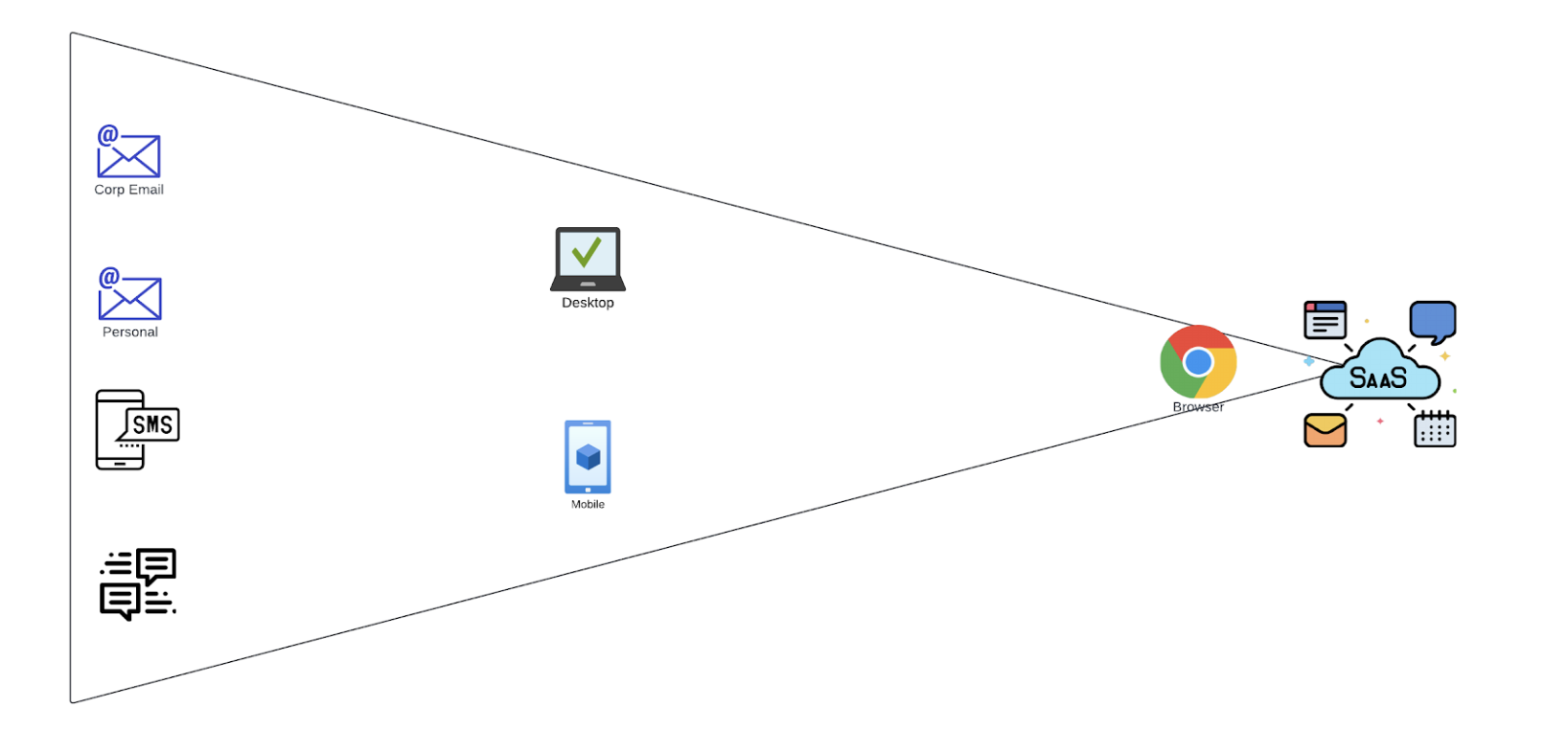
Phishing attacks span multiple layers of the tech stack, including:
- Phishing channels: Corporate email, personal email, SMS, messaging apps.
- User devices and clients: Corporate desktops, personal devices, browsers, apps.
- Networks: Corporate, home, and public networks.
- SaaS applications: The ultimate target, where credentials are used to gain access.
The permutation of these tech stacks creates many attack paths, and the complexity of securing every layer grows exponentially. This underscores the need for robust security architecture.
Building an Effective Defense
To defend against phishing, organizations must evaluate their security controls across all layers. A key strategy is to identify choke points—critical areas that attackers cannot bypass. In SaaS environments, two natural choke points emerge:
- The SaaS application: Monitoring and logging every interaction at the application layer ensures visibility into any suspicious behavior.
- The browser: Most SaaS interactions occur through a browser, making browser security essential in preventing phishing attacks.
At Obsidian, our strategy focuses on these choke points. Our browser extension provides real-time phishing detection and administers warnings when users visit malicious sites. If an attack slips past the browser extension, our detection systems analyze SaaS activity logs to identify suspicious behaviors, stopping potential breaches before they escalate.
Final Thoughts
Phishing attacks are evolving, with attackers finding creative ways to bypass traditional defenses. A layered approach that secures critical control points—such as the browser and SaaS applications—is key to preventing account takeovers and protecting against identity-based threats. Combining browser-based protection with SaaS monitoring and conditional access policies offers a strong defense against even the most sophisticated phishing attempts.




