Introduction
Due to the growing importance of securing local access in SaaS applications, we recently posted a blog discussing the complexity of enforcing Single Sign-On (SSO) within Salesforce and the frequent misconfigurations we encounter at Obsidian Security. A striking statistic from our observations: 60% of Obsidian’s customers initially have local access without Multi-Factor Authentication (MFA) configured for Salesforce. This is a significant security gap that Obsidian works diligently with customers to secure.
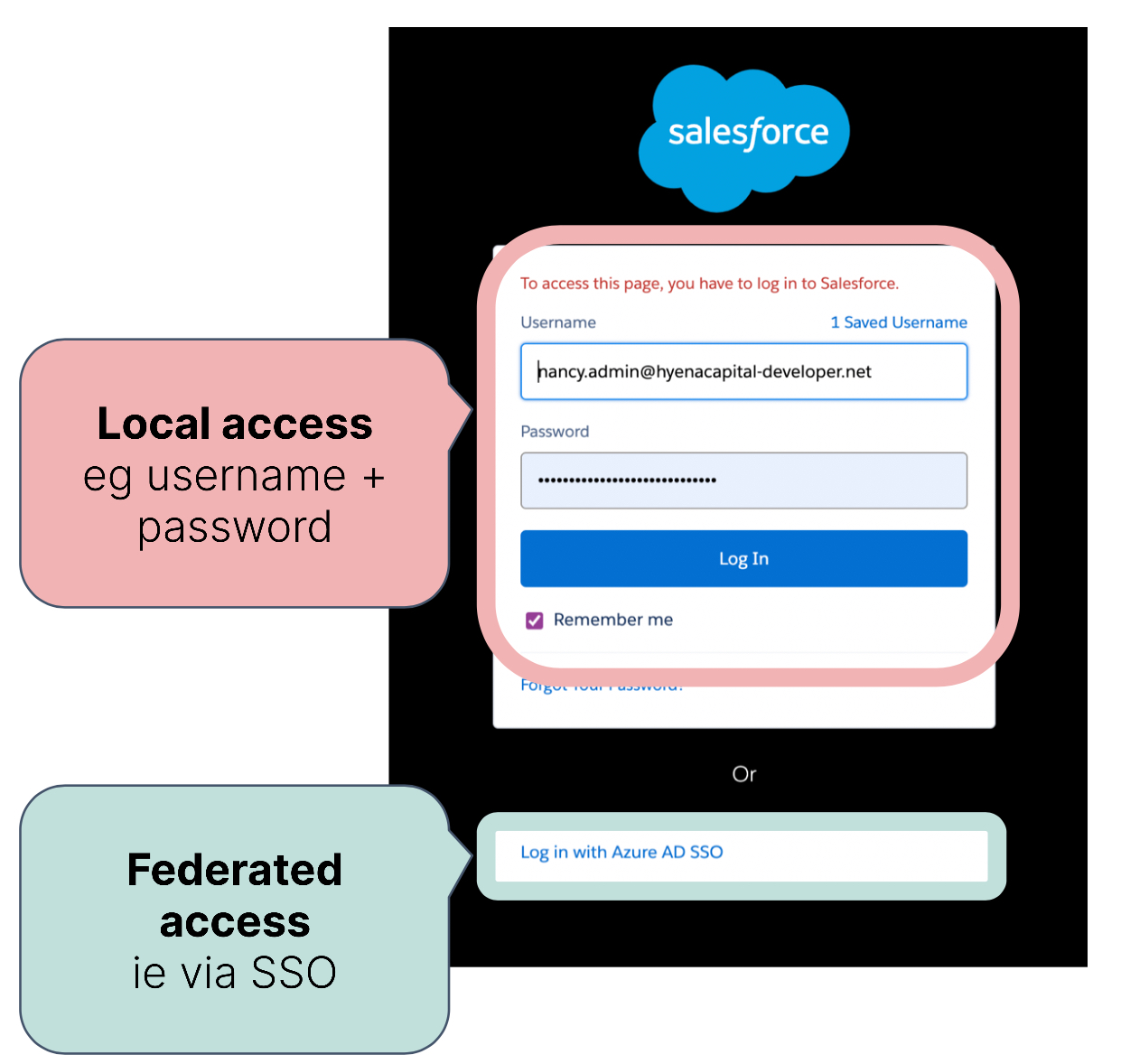
The Hidden Vulnerability of Local Access
One of the interesting observations we make is that application owners who manage Salesforce daily are often unaware of this misconfiguration. Despite their deep knowledge of Salesforce management, local access without MFA remains an overlooked vulnerability. If this is true for Salesforce, it raises concerns about the state of other SaaS applications, especially those without developed expertise or knowledge.
Attacker Focus and Trends
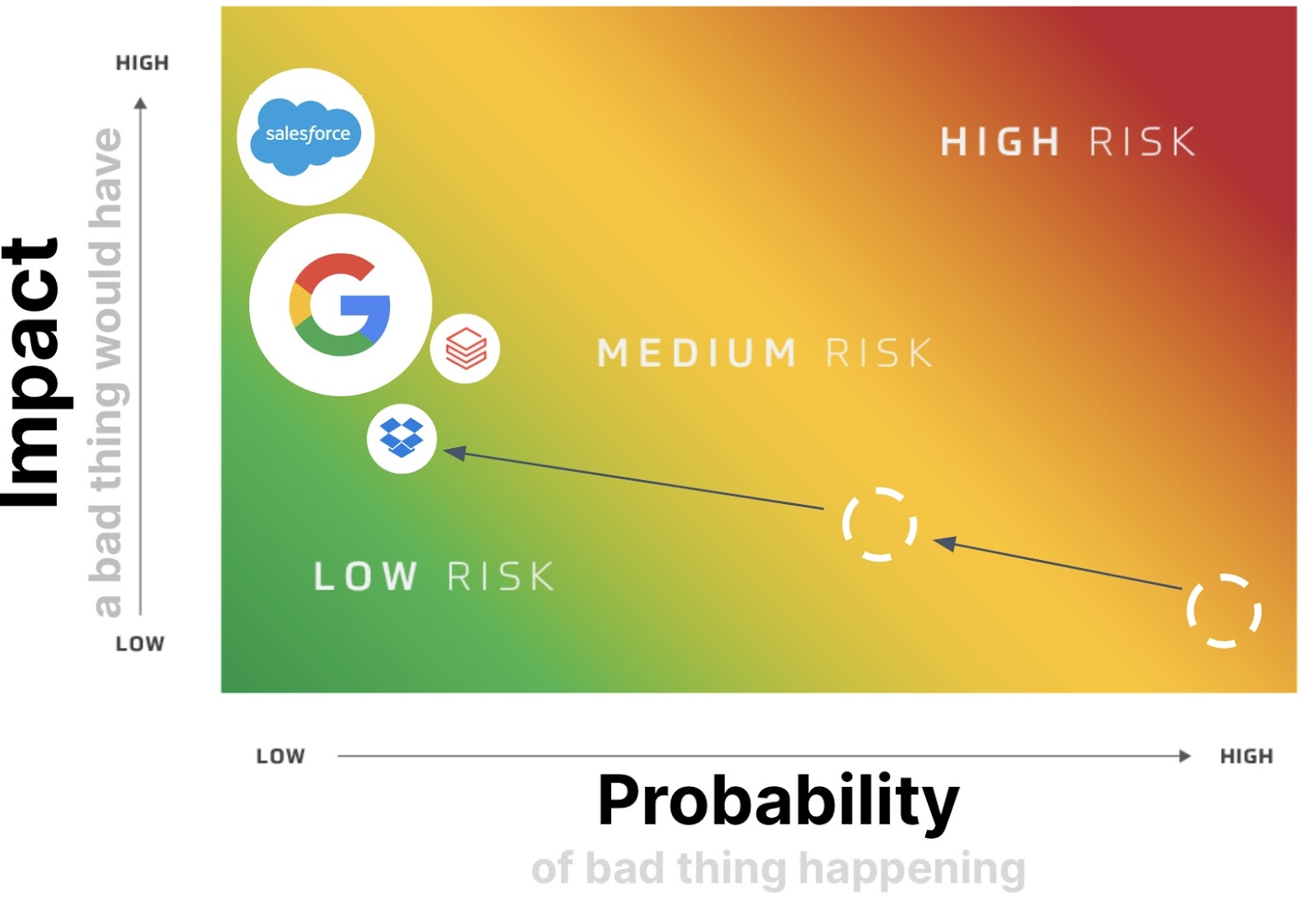
Historically, attackers have concentrated on the Identity Provider (IdP) space, targeting providers like Okta, Microsoft Entra, and Ping. This focus is due to several reasons:
- Maximal Impact: By compromising an IdP, attackers can gain broad access across multiple applications.
- Efficiency: Developing expertise to breach a handful of IdPs is more efficient than learning the diverse local access pathways of numerous SaaS vendors.
Over the past 12 months, nearly 100% of the breaches where companies sought our help through CrowdStrike or other incident response partners were IdP-focused. Notably, 70% of these breaches involved subverting MFA, often through methods like SIM swapping. In instances where local access bypass the IdP exists (aforementioned 60% of customers), we observe that 95% of the time it has no MFA.
However, with recent discussions around Snowflake, the topic of “shadow authentication” is gaining traction among attackers. We define shadow authentication as the existence and use of unsanctioned means to authenticate a user within an application, as in the case of local authentication described earlier. Obsidian Security has observed an increase in bruteforce attacks against SaaS applications via local access pathways over the last two weeks, indicating a growing awareness of this attack vector.
Future Expectations
Given that attackers are always looking for the easy and most efficient pathways, we anticipate that in the next 12 months, local access or shadow authentication will become a major attack path. As attackers shift their focus, organizations must be proactive in securing these pathways.
What You Can Do to Secure Local Access
- Discover SaaS Applications: Establish a program for discovering SaaS applications, especially those containing sensitive data or integrating with applications holding sensitive data.
- Evaluate and Secure: Decide whether to eliminate or integrate these applications into your IdP. If retained, ensure that SSO and MFA are enforced for the majority of users. Document the reasons for any accounts that do not align with the policies. These high-risk accounts need additional monitoring.
How Obsidian Helps
Obsidian Security offers robust solutions to address these challenges:
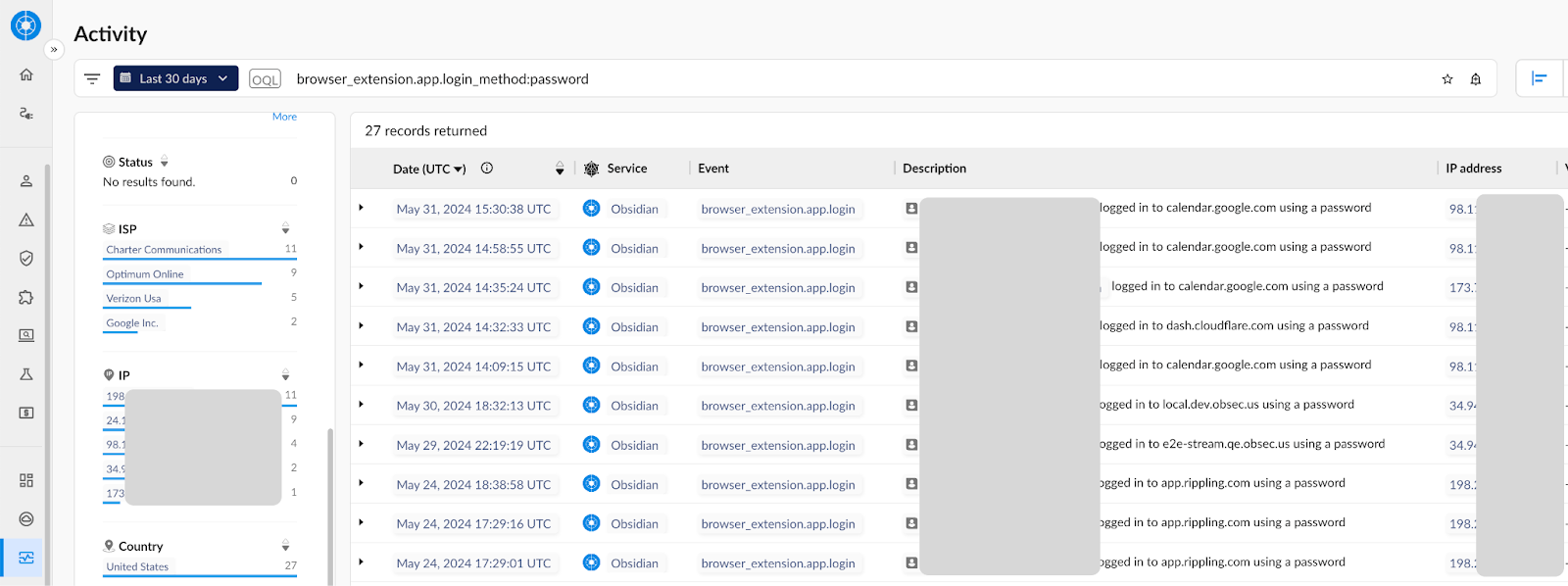
- Discovery: Through our browser extension, email header scanning, and as they integrate via OAuth into your core SaaS apps – with the end result that we detect SaaS applications early in their life cycle.
- Monitoring: Our patented browser extension allows us to monitor when users access applications locally – bypassing the IdP.
- Prevention: This early detection enables us to identify and block potential attack pathways before they can be exploited. Both by locking down local access, but additionally by adding a layer of data governance and application hardening.
Securing local access in SaaS applications is important. By leveraging Obsidian’s capabilities, organizations can enhance their security posture, protecting against the evolving threats targeting local access and shadow authentication.
For a more detailed analysis, read our original blog post here.