In today’s digital-first world, individuals are bringing B2C behaviors into the B2B sphere. Just as someone might casually share personal login details with platforms like Turbotax for tax filing, many are now sharing corporate credentials with third-party providers, for various personal and professional tasks, compromising identity security.
Moreover, a recent investigation by Obsidian’s Threat Research team has shed light on the risks associated with this trend. They detected a critical risk associated with Argyle—a service that facilitates employment and income verification and payroll management by integrating with HR Management (HRM) systems through credential flow.
Why it matters
Argyle’s service presents a significant risk to organizations due to its insecure integration via credential flow. If compromised, this integration provides an uncontrolled pathway for accessing sensitive data, thereby undermining identity security.
From Obsidian’s investigation thus far, this Argyle risk affects over 800 G2000 companies and numerous others through their HRM systems and Identity Providers (IdPs).
Investigation overview
Obsidian’s Threat Security Research team observed the following suspicious sequence of events across multiple tenants:
- An unknown identity is authenticated through an employee’s Identity Provider (IdP) account via anonymous proxy infrastructure with Multi-Factor Authentication (MFA) approval.
- Following authentication, the identity employed Single Sign-On (SSO) to gain access to the company’s Human Resource Management (HRM) system, which may have included platforms like Workday and PeopleSoft.
- Our telemetry data reveals that within the HRM system, the identity traversed sensitive employment and income information and, in some instances, altered payment elections.
This activity resembles common identity threats, such as gaining initial access through an access broker or carrying out complete payroll theft following an account takeover.
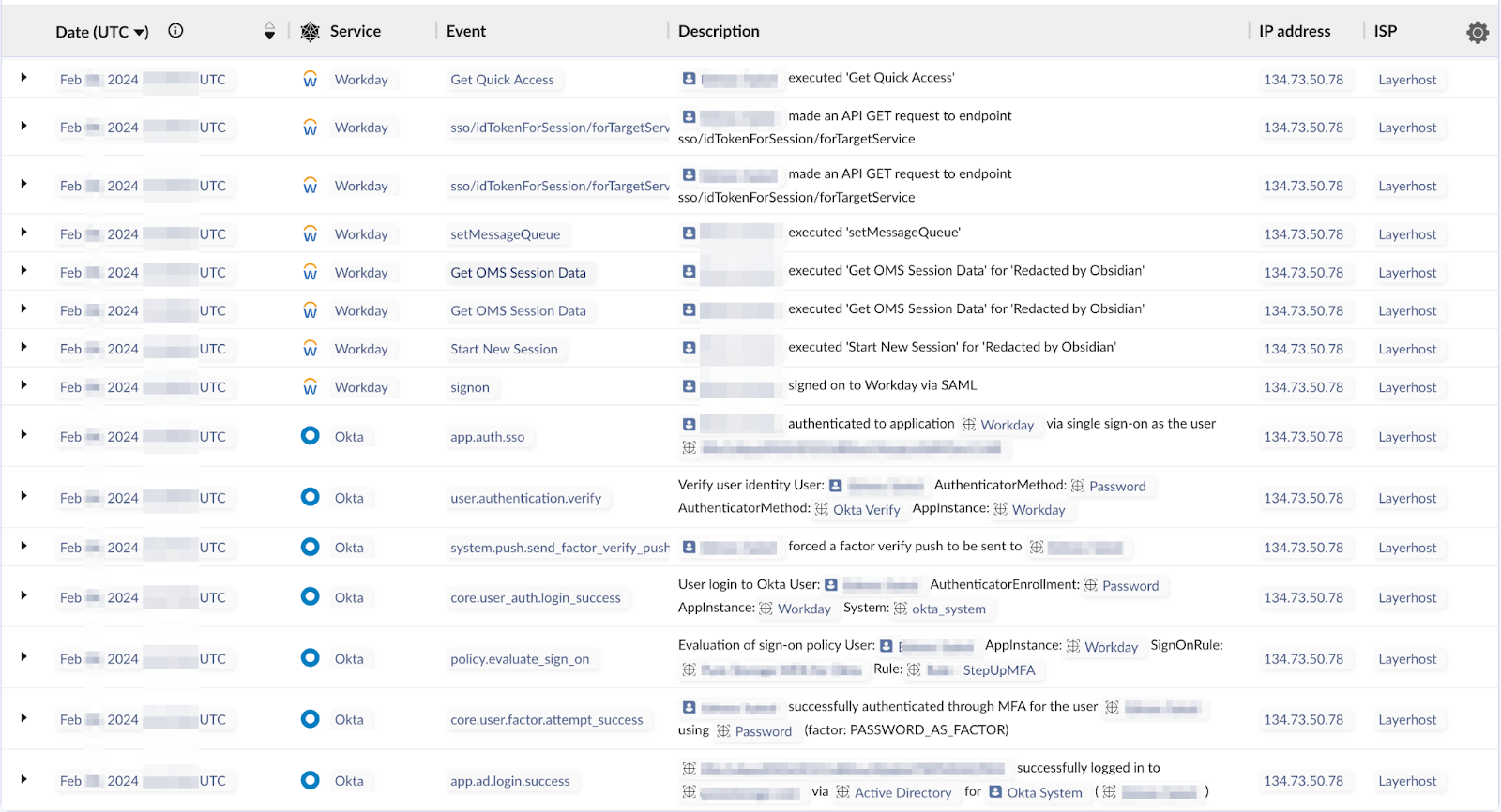
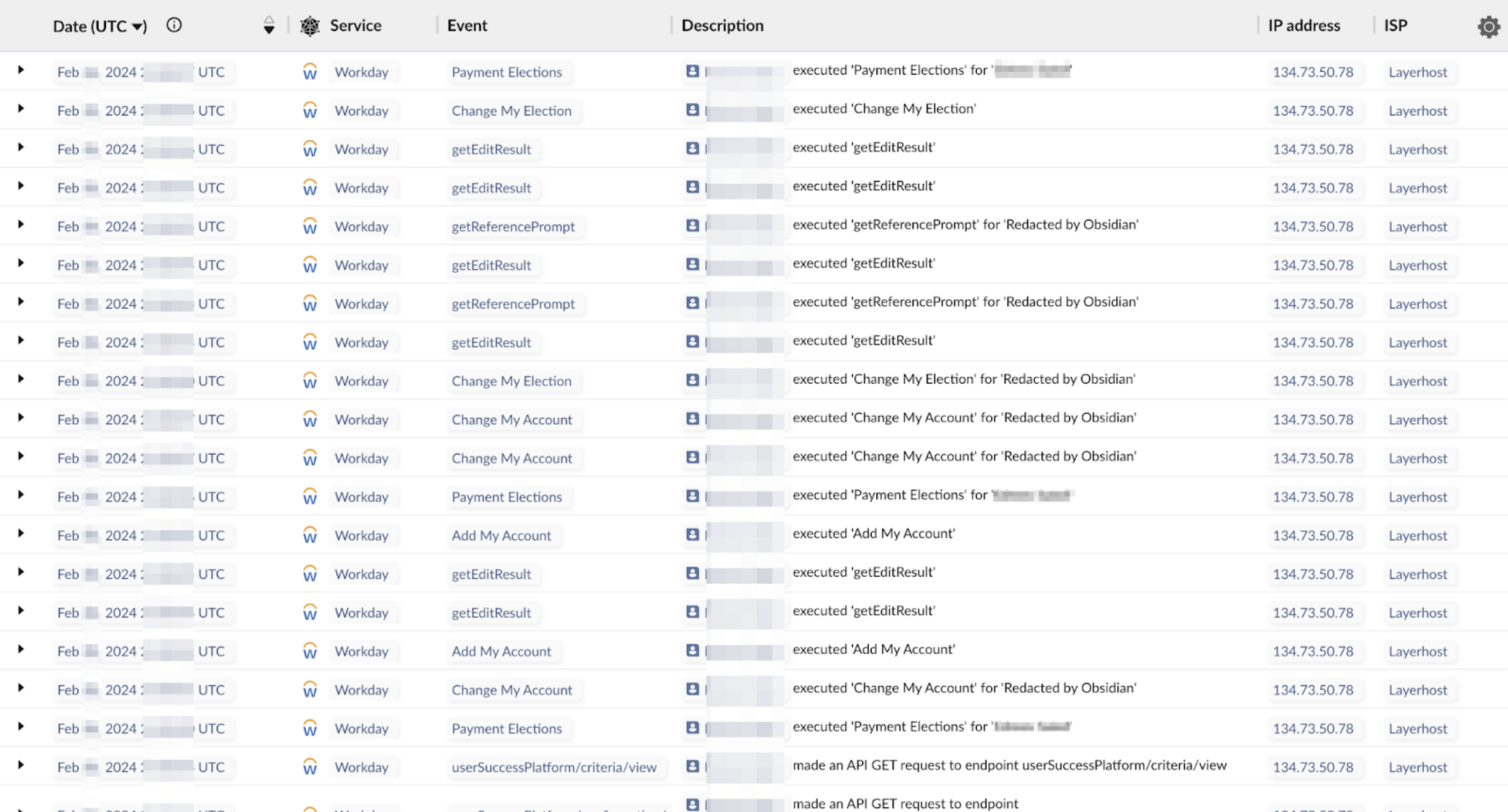
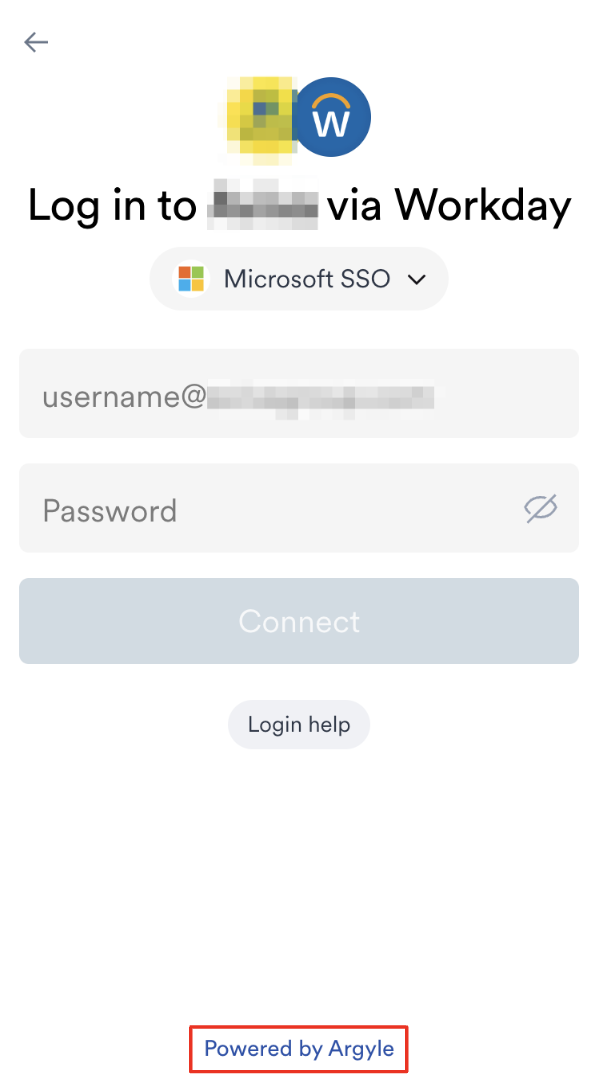
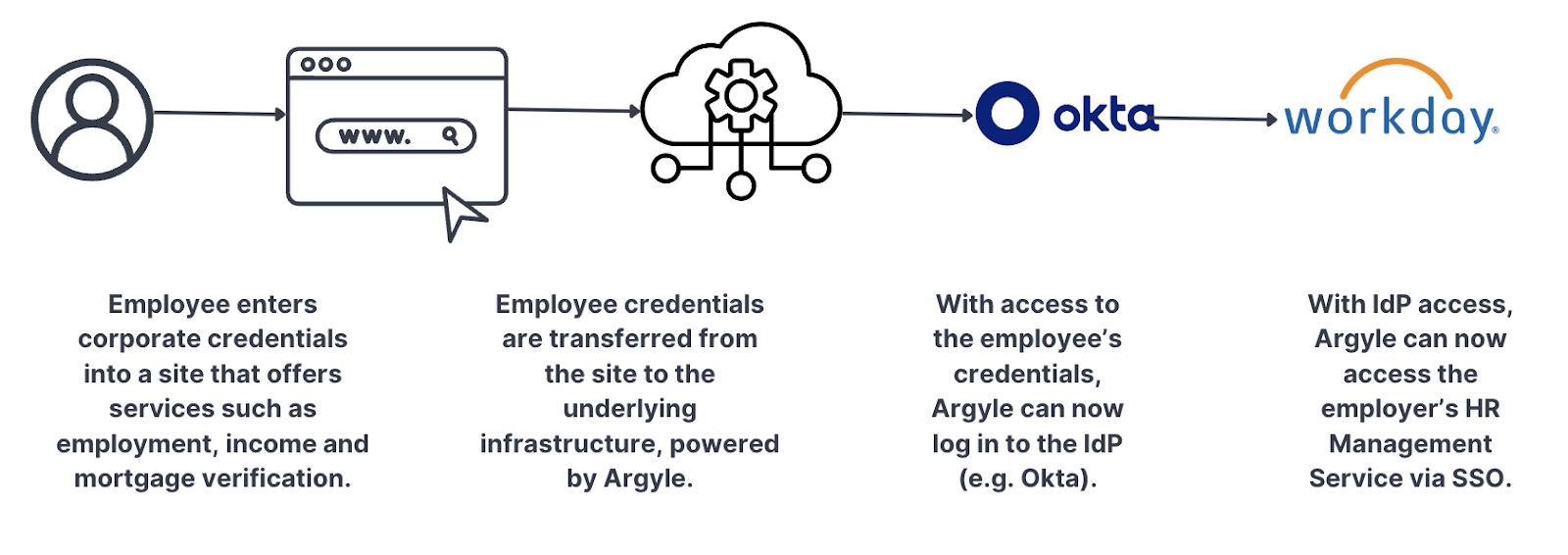
The suspicious activity illustrated above was traced back to Argyle. Below, we have outlined how this activity unfolded, starting with the employee entering their corporate credentials into a third-party site, through to Argyle gaining access to both the IdP and HRM service.
Security implications
Although there hasn’t been any observed exploitation, the integration facilitated by Argyle raises various security concerns around identity risks. These include:
- Credential Harvesting: Argyle prompts employees to directly submit their corporate identity credentials (username and password) into their platform, exposing credentials to a 3rd party with an unknown security posture.
- MFA pass-through: In cases where multi-factor authentication (MFA) is implemented, users may willingly provide additional authentication factors, training people to subconsciously provide MFA to 3rd party.
- Session Hijacking: Once Argyle completes the authentication flow, they possess a set of valid session tokens, giving them persistent access to the IdP and HRM system. These tokens, especially the IdP tokens, are typically privileged to navigate to various SaaS applications federated. It is not unreasonable to think of a potential incident like the Okta HAR one that happened not long ago.
Blast radius
A variety of HRM services and IdP solutions are implicated by this risk due to their integration with Argyle.
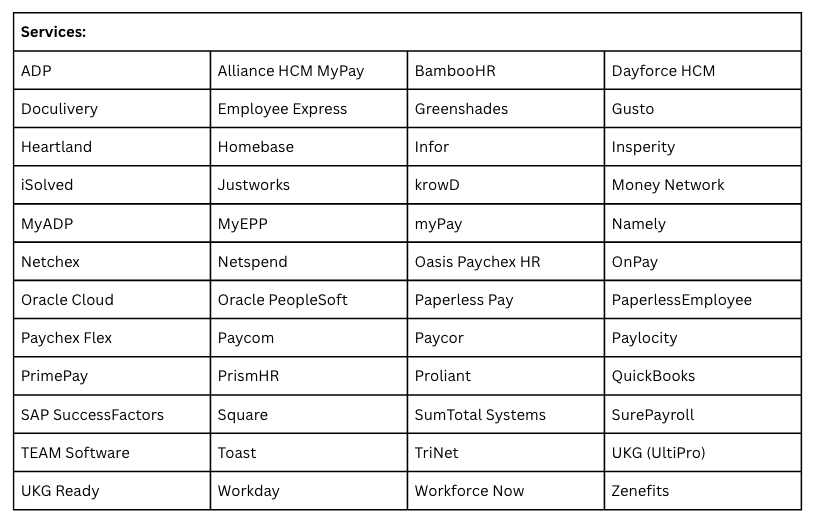
IdPs:
- Cyberark
- Duo
- Logingov
- Microsoft
- Okta
- OneLogin
- PingID
- SecureAuth
What should I do to protect my organization?
Unlike the classic identity threat via account takeover, individuals willingly engage in these processes, making self-reporting unlikely. Even strong MFA based on WebAuthN may fall short if weaker methods like SMS or TOTP are allowed to be downgraded. Therefore, continuous monitoring of corporate identity threats becomes paramount to detect and mitigate risks.
Obsidian recommended actions
To enhance security and mitigate risks, we recommend taking the following actions:
1. Deploy Obsidian’s new detection rule:
- Implement the new threat detection rule named “Credential and Cookie Leakage via HRM Credential Flow Integration.” This rule is designed to help identify access to your SaaS by Argyle.
- Set up an action policy on this rule to receive notifications for quick response.
- To learn more on detecting threats pre-exfiltration, check out this page.
2. Review audit logs:
- Check your audit logs in Obsidian’s Activity Timeline or your SIEM for any Indicators of Compromise (IoCs) or identity risks.
3. Identify and take action for exposed accounts:
- Identify accounts that have been part of the credential flow and take immediate action by resetting passwords, IdPs (Identity Providers), and HRM system sessions.
What identity risks should vendors look out for when implementing 3rd party services?
There’s no denying the value provided by tools that automate traditionally manual processes like employment and income verification. However, as this identity risk scenario highlights, services must undergo careful assessment to safeguard your organization’s security.
OAuth addresses these needs by authorizing access to user-owned resources without exposing credentials to third parties.
Moreover, secure integration should adhere to the principle of least privilege, requesting only essential information for validation (e.g., employment or income status). It should avoid accessing sensitive data such as pay slips or W2 forms. Our examination of HRM systems revealed challenges in meeting these requirements due to the broad access permissions available, sometimes limited to read/write access across all resources.
Appendix (indicators of compromise)
Identified IP addresses:
Most incoming traffic originates from proxy providers. Notable IP addresses observed over the past month include:
- 23.239.180.0
- 23.239.180.222
- 38.18.13.14
- 38.18.27.167
- 38.18.29.189
- 45.41.128.138
- 45.41.129.228
- 45.41.130.11
- 45.41.130.33
- 45.56.133.243
- 45.56.135.174
- 69.30.86.206
- 104.148.106.180
- 104.194.195.228
- 104.222.33.7
- 104.223.191.132
- 104.223.243.61
- 134.73.19.130
- 134.73.19.222
- 134.73.22.51
- 134.73.22.82
- 134.73.23.143
- 142.111.138.14
- 142.111.138.174
- 142.111.185.67
- 154.30.105.167
- 154.30.107.245
- 154.30.109.32
- 154.30.109.132
- 154.30.109.159
- 157.52.171.208
- 157.52.171.253
- 157.97.126.156
- 158.222.113.112
- 158.222.117.42
- 167.160.50.21
- 167.160.50.249
- 185.176.51.75
- 185.176.51.190
- 192.30.80.86
- 192.30.80.155
- 207.199.173.96
- 207.199.188.146
- 209.147.81.82
- 209.147.81.175
User agent strings:
The user agent string linked to the activity may vary over time but frequently repeats:
- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36
- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.15 Safari/537.36
- Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4469.0 Safari/537.36
- Mozilla/5.0 (iPhone; CPU iPhone OS 16_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/16.1 Mobile/15E148 Safari/604.1
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like




