Earlier this month, Twilio shared publicly that they had been targeted with an ongoing social-engineering phishing scam via SMS. This is the latest in a string of recent sophisticated breaches gaining access to internal systems such as the Okta LAPSUS$ hack and adversary-in-the-middle (AiTM) attacks.
While the Obsidian organization and our platform are not directly impacted by this incident, several of our own customers were understandably concerned that they might have been affected. In this blog, we recount how Obsidian customers leveraged our platform to promptly respond to the Twilio incident, provide some guidance on potentially malicious activities to watch out for, and share our team’s thoughts on trends manifesting across recent account compromises at several organizations.
Twilio hackers compromise over 130 organizations with ‘oktapus’ phishing kit
Twilio, a leading customer engagement platform, notified approximately 125 customers that their data had been accessed by malicious actors in a recent phishing attack on August 7th, 2022. The attackers gained access to Twilio’s customer support console by stealing employee login credentials through SMS messages. These texts impersonated their IT department and included malicious URLs prompting former and current employees to falsely update their SSO credentials, using words like Okta, SSO, or Twilio.
The hackers responsible have been very successful, hitting over 130 other organizations such as MailChimp, and Klaviyo. Customers using these services were consequently targeted with supply-chain attacks including Signal and DigitalOcean. The most recent update from Twilio on August 10th asserts that attackers have continued their social engineering efforts, as such, Twilio will not be providing further information at this time.
How to tell if you’re being targeted and respond with swift accuracy
Around the time that the Twilio incident was announced, some Obsidian customers began to suspect that they had fallen victim to a similar breach scenario. Several of their employees began receiving suspicious text messages containing a malicious URL that appeared to point to a credential harvesting website aiming to gain access to their Okta environment.
Acting on this suspicion, their team began to review their Okta logs to identify any questionable activity. Upon doing so, they observed numerous requests from user accounts to enroll new devices for multi-factor authentication (MFA) and deactivate existing trusted devices.
While not inherently malicious behavior on its own, the registration of a new device for MFA allowed our customer to begin investigating potentially compromised user accounts. Within minutes, Obsidian’s custom detection capabilities were leveraged to trigger anytime new MFA devices were successfully enrolled in Okta which signaled the successful enrollment of a new device for MFA. This enabled the swift identification of employees who may have fallen victim to the SMS phishing attack. With a cohort of potentially compromised users easily identified, they focused their time on investigating each individual from within the Obsidian portal.
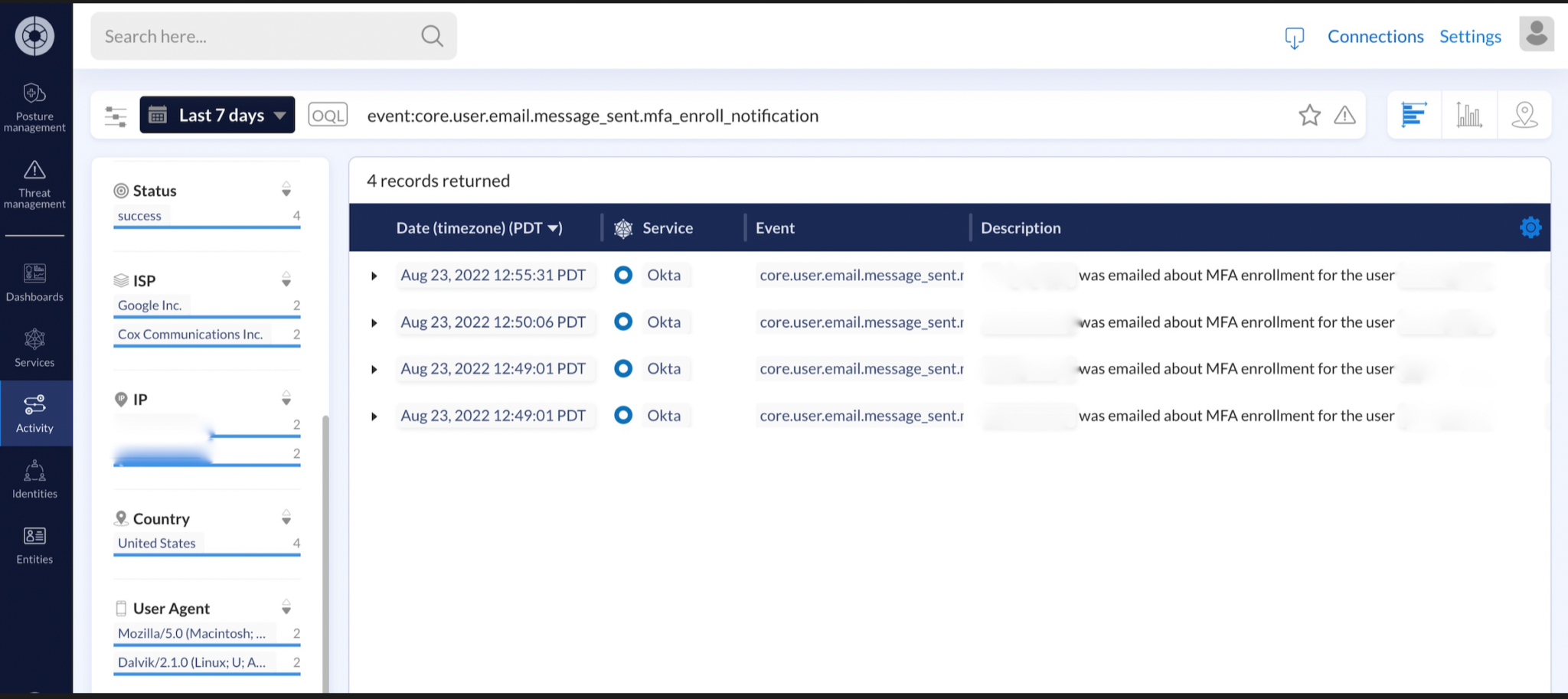
Our customers leveraged Obsidian user dashboards and custom detections to stay ahead of potentially malicious activity from accounts with unusual client details. The platform’s built-in threat detection models like impossible travel were also critical for providing further evidence of compromised accounts. The ability to easily pivot and investigate all relevant contexts for a compromised user—their accounts, events, and activities—throughout the SaaS environment significantly reduced the time and effort required for thorough incident response. Compromises were quickly identified, and security teams were able to effectively respond.
A Changing Face of Compromise
Businesses have collectively moved into a “SaaS forward space,” entrusting an unprecedented amount of sensitive data to a proliferation of cloud applications. With adoption continuing to expand, protecting these services and the IDPs that validate access to them has never been more business-critical. SaaS complexities and resulting visibility gaps introduce significant risks to your business that cybercriminals are actively exploiting. A wealth of sensitive data combined with immature control and detection frameworks make SaaS a prime target. To respond quickly and confidently, security teams need a way to make sense of their noisy SaaS environments and identify threats across applications.
That’s why Obsidian sees threat mitigation as an absolutely critical component of SaaS security posture management (SSPM). Our team is committed to the continuous development of cutting-edge machine learning models that drive our world-class SaaS threat detections. With security teams already stretched thin by a monumental workload, it’s important to us that Obsidian offers immediate and clear investigation and remediation of SaaS threats without requiring the significant effort of deploying agents, building custom rulesets, or tuning detections.




